Cyber threat intelligence is becoming a key component of a modern organization's cybersecurity strategy.
An effective cyber threat intelligence strategy plays a critical role in ensuring that an organization remains safe from cyber attacks.
With cyber threat intelligence, organizations must have the ability to continuously collect and analyze the information they need to identify and respond to threats.

But what is cyber threat intelligence we're talking about here?
Definition of cyber threat intelligence
In 2013, Gartner Research defined threat intelligence as follows.
"Threat intelligence is evidence-based knowledge, including context, mechanisms, metrics, impact,
and actionable advice, about existing or emerging threats or risks to assets that
can be used to inform decisions about an entity's response to those threats or risks."
To summarize, threat intelligence is
knowledge based on a variety of data and information for threat response.
Data, information, and intelligence
To understand threat intelligence, it's important to recognize three distinctions.
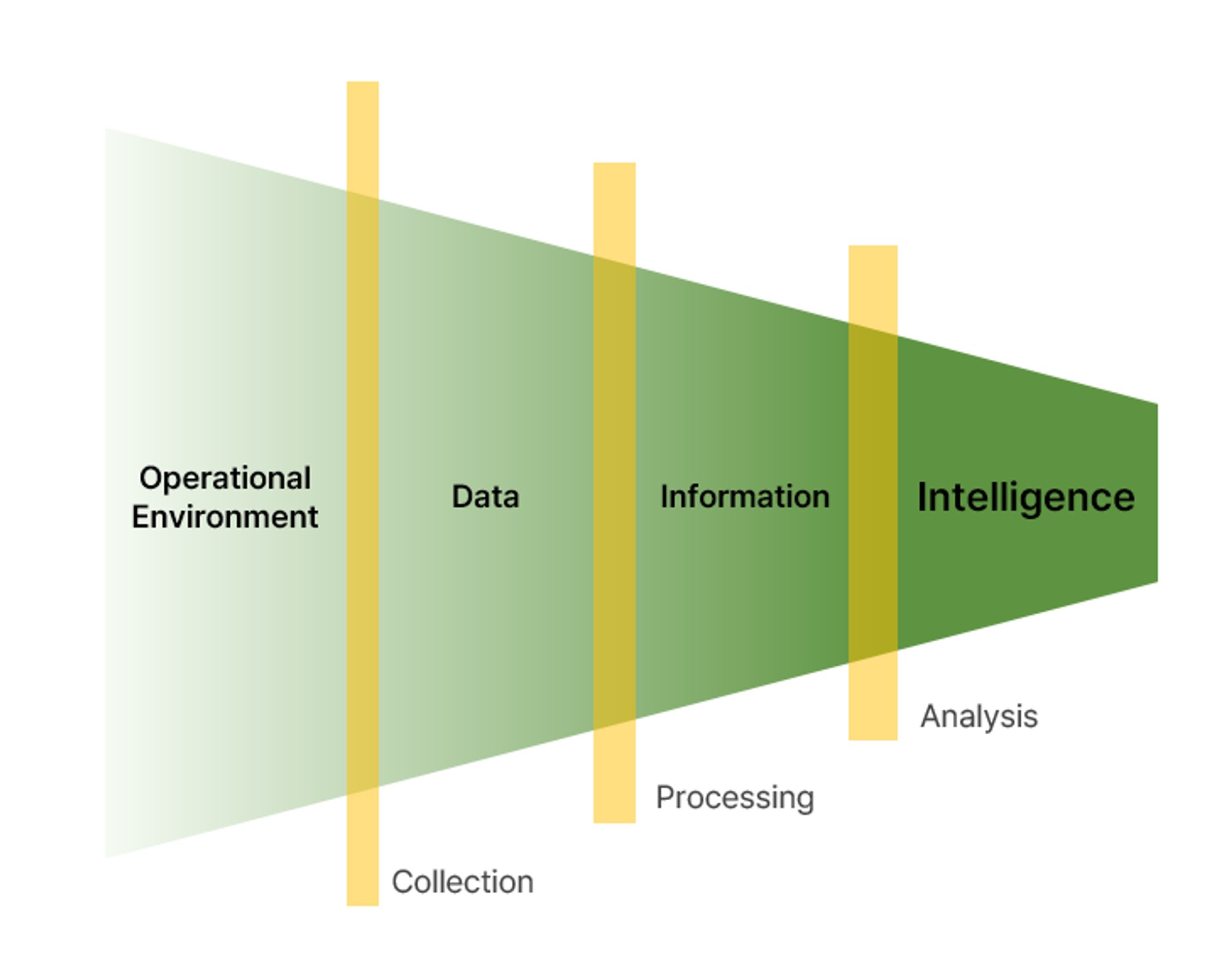
Data
Data is simply raw, unprocessed material that has been collected.
It's usually simple metrics like IPs, URLs, and hashes, which don't tell us much without analysis.
Information
Information is data that has been analyzed and processed to make it meaningful.
It's more useful than data because it tells you what type of data it is, but it still doesn't directly tell you what to do.
Intelligence
Intelligence is the result of analyzing and processing a variety of collected data and organizing it into meaningful information within a specific context.
The pain pyramid
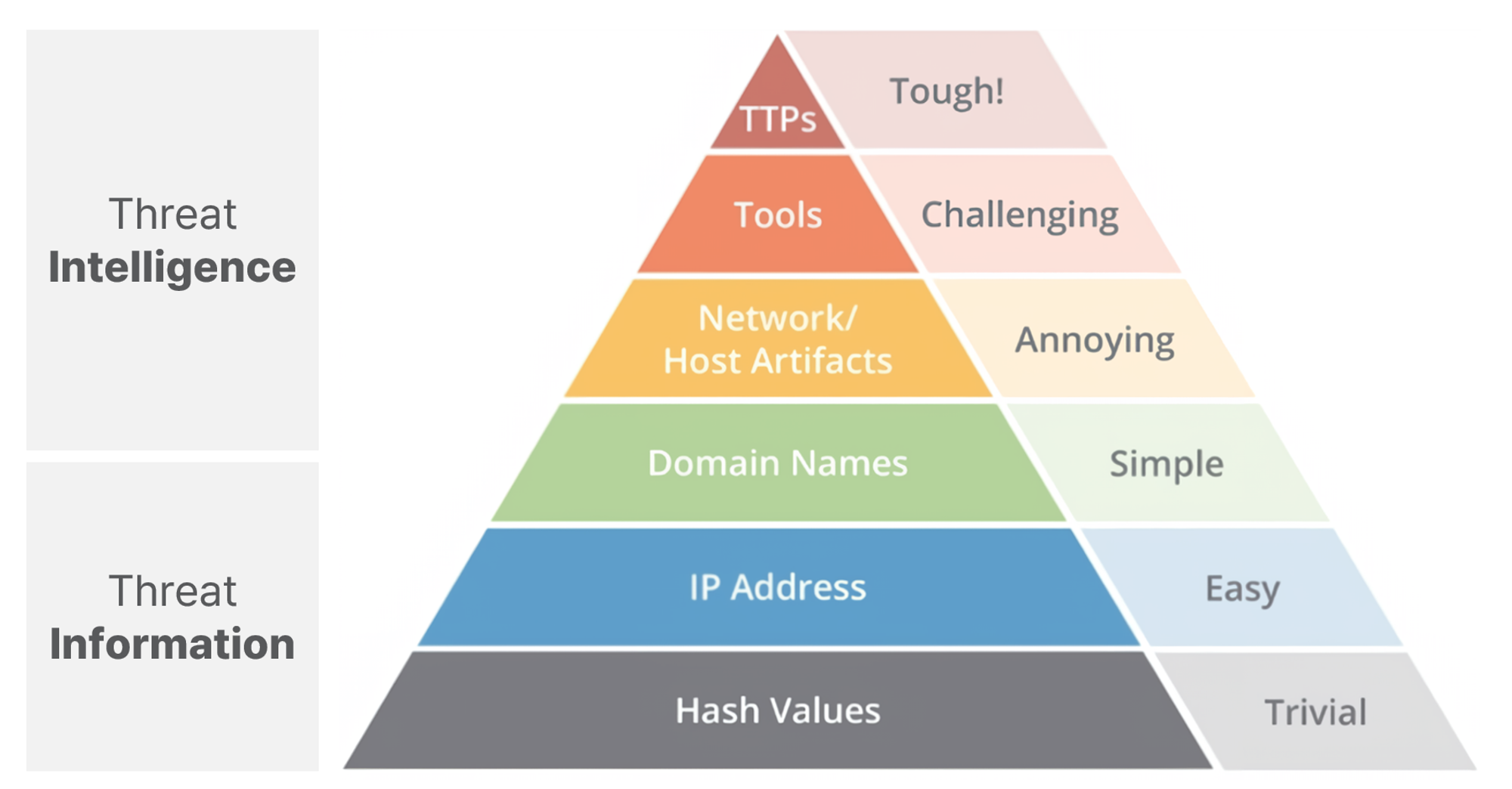
The "Pyramid of Pain" is an illustration often used to describe threat intelligence.
First introduced in 2013 by security expert David J. Bianco, it is a concept often used to describe how to effectively utilize intelligence.
The TTP at the top of the pyramid is said to be the most effective in defending against attacks.
Each stage represents an attacker's stress along with indicators.
Each step represents the stress on the attacker when the threat metric is blocked.
Level 1 : Hash Values
Level 1 'Hash Values' says that the stress on the attacker is trivial.
This is because hash values can be easily tampered with.
Level 2 : IP Address
Level 2 'IP Addresses' says the stress to the attacker is easy.
This is because IP addresses can be easily changed using proxies, etc.
Level 3 : Domain Names
Level 3 'Domain Names' says ’simple' because they are easy to change using proxies, etc.
This is because many DNS service providers have relaxed registration criteria, making it simple to change domains.
Level 4 : Network/Host Artifacts
'Network/Host Artifacts' says the stress for attackers is Annoying.
Level 5 : Tools
‘Tools' says Challenging.
This is because when an attack tool is blocked, it requires effort to bypass it, such as modifying code or developing new code.
Level 6 : TTPs
Level 6 ‘TTPs' says the stress on the attacker is Tough.
A TTP is a tactic, technique, or procedure, a process that includes all the steps from launching an attack to achieving its objective.
Bypassing it requires a significant level of cost and time, including the need to devise new techniques or procedures.
Therefore, it is said that the higher up the chain you defend, the more effective your defense will be.
MITRE ATT&CK
The MITRE ATT&CK Matrix is a visualization of the concept of TTP at the top of the aforementioned pyramid of pain.
TTP stands for Tactics, Techniques, Techniques, and Procedures.
The MITRE ATT&CK Framework identifies over 260 techniques along with 14 tactics.
The TID detail page for each technique includes
examples of procedures, countermeasures, detection methods,
and reference sites to help you defend against these attacks.
Lifecycle
Deriving threat intelligence typically involves the following processes.
The life cycle of threat intelligence is the process of transforming raw data into finished intelligence for decision-making and action.
It starts with requirements and moves through collection, processing, analysis, distribution, and feedback in a closed loop.
Requirement → Collection → Processing → Analysis → Dissemination → Feedback
1. The Requirements phase sets roadmaps and objectives for threat intelligence operations.
2. The collection phase collects a large amount of threat information from a variety of sources.
3. The processing phase preprocesses the collected data in a format suitable for analysis.
4. The analysis phase draws answers to the requirements.
5. The deployment phase deploys the analyzed results.
6. The feedback phase receives feedback on the results you distribute.
This threat intelligence lifecycle helps organizations systematically manage
how they collect, analyze, share, and leverage a variety of information to counter security threats.
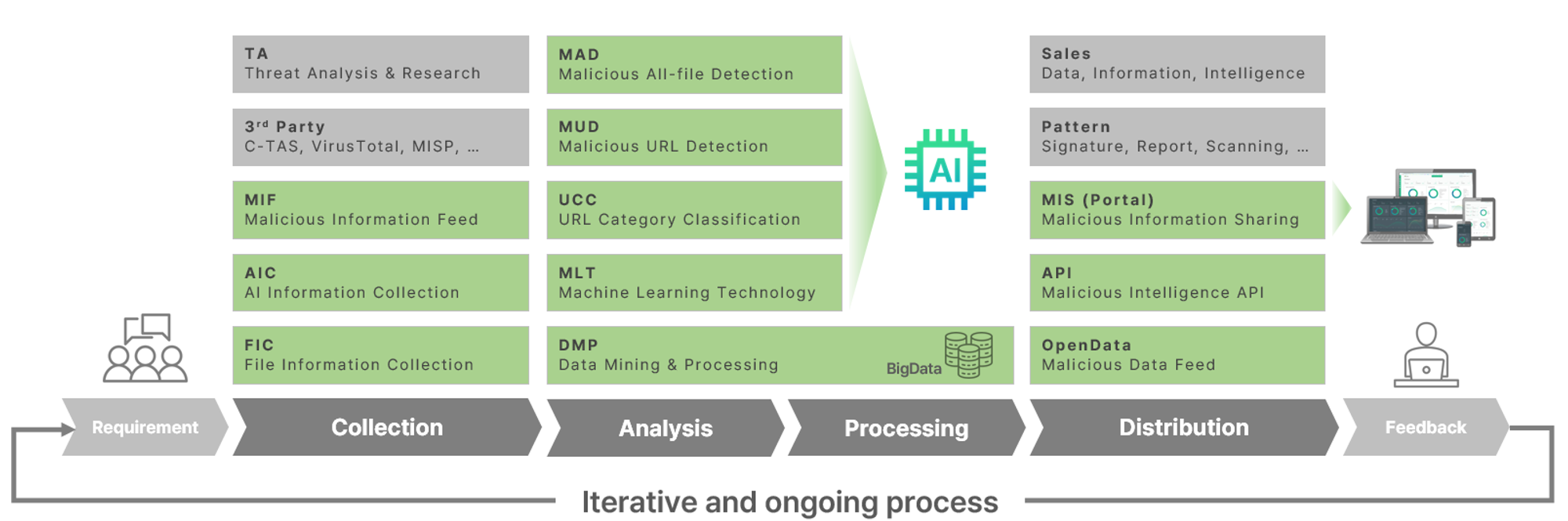
The life cycle of MONITORAPP's AILabs is not much different from that of common threat intelligence.
It operates as a continuous, iterative process, starting with requirements,
followed by collection, analysis, processing, distribution, and feedback.
Requirement → Collection → Analysis → Processing → Distribution → Feedback
The core is an analysis and processing system based on AI and big data,
and a web-based portal that provides various information visibly.
You will find more details in Part 3, 'AILabs Cyber Threat Intelligence Platform'.
The need
So, why do we need threat intelligence?
Cyber threats are sophisticated in many ways, and attackers don't just launch one-off attacks, but persistent attacks directed at specific targets.
In order to defend against advanced persistent attacks, often referred to as unknown threats,
traditional passive responses based on fragmented data and information are not enough, and threat intelligence is required.
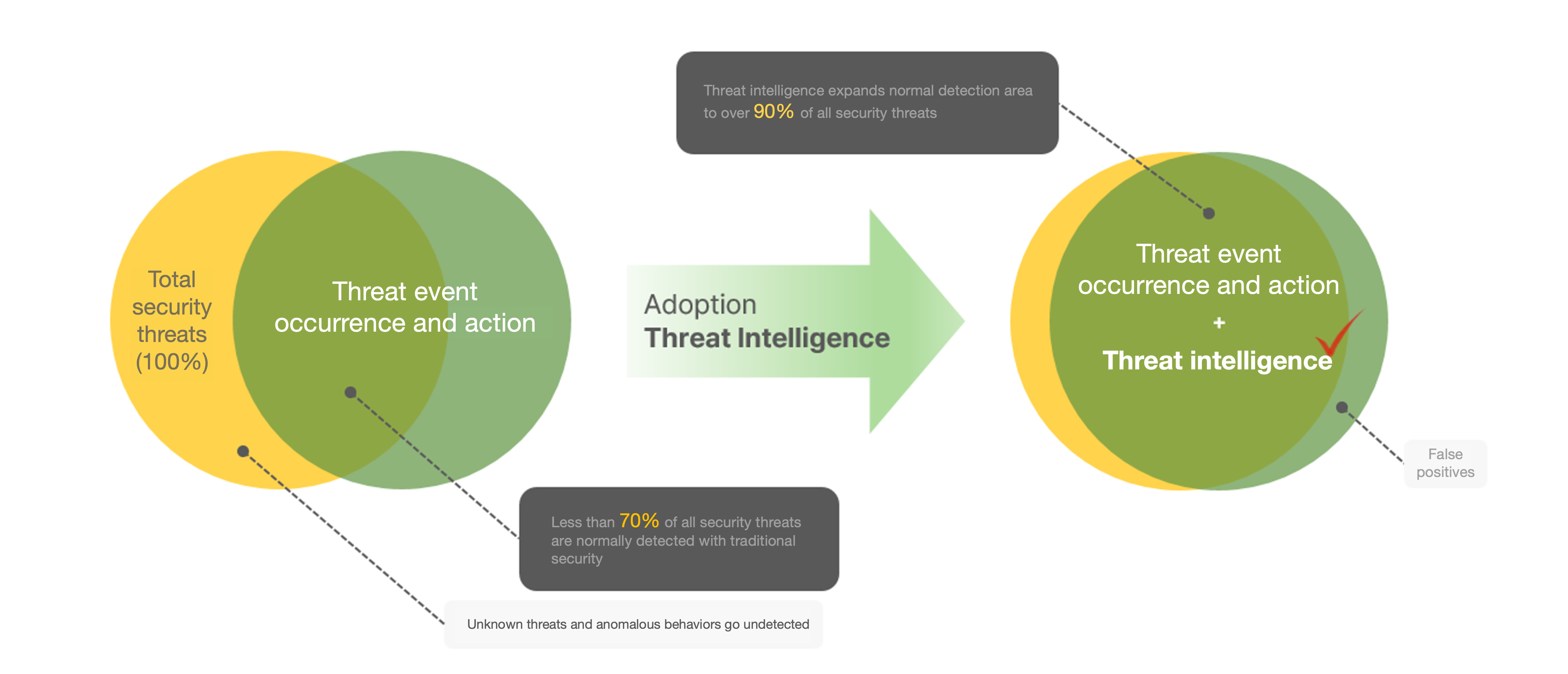
If the overall security threat is 100%, less than 70% of the area can be detected normally with traditional security.
Other parts are undetected areas for unknown threats and abnormal behavior,
and a significant proportion of threat events may be false detections.
With the help of threat intelligence, the false positives and undetected areas can be significantly reduced,
and the positive detection area can be expanded to 90% or more.
AILabs, MONITORAPP's cyber threat intelligence platform
AILabs is a cyber threat intelligence platform developed and operated by MONITORAPP.
It is an integrated security platform that provides threat intelligence by big dataizing unstructured threat data
collected from feed channels of various roots and providing multi-dimensional analysis and
refinement with an advanced engine that includes artificial intelligence.
In the next chapter, we will learn more about AILabs.
Thank you.