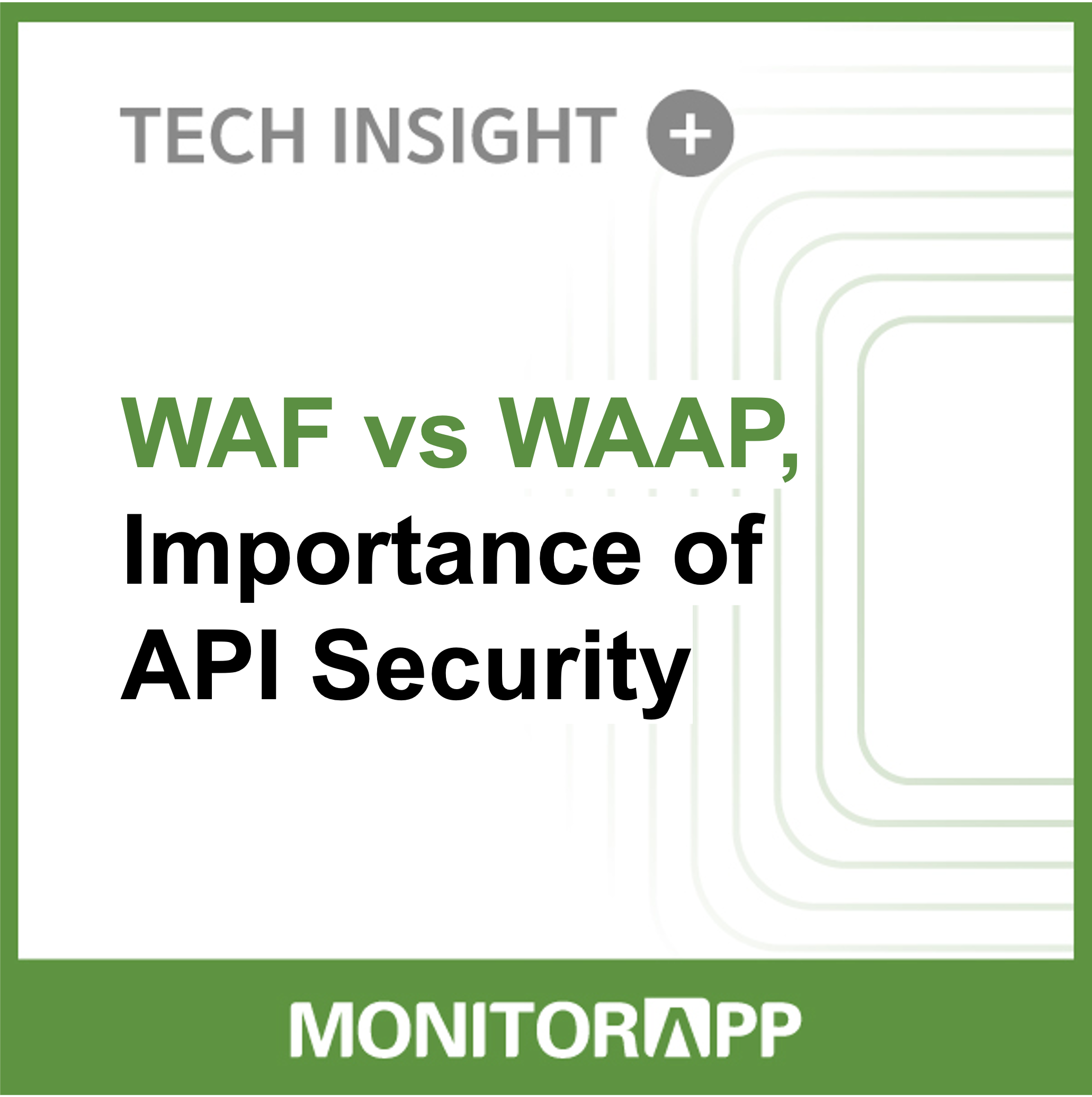
WEB Application Firewall (WAF) has been a representative and traditional primary tool for enhancing web application security.
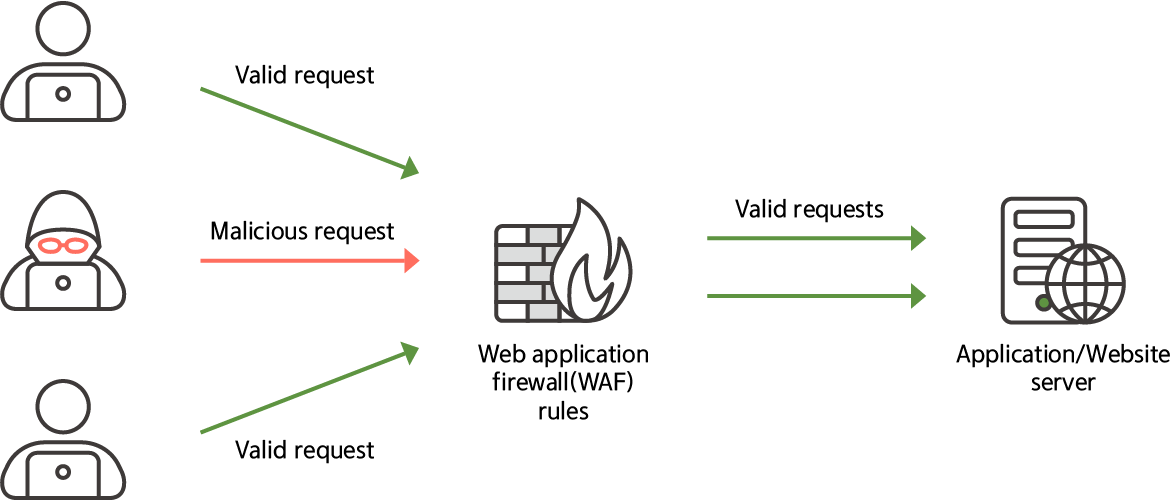
However, with recent advances in web technology, API usage has exploded and API threats have increased proportionally, highlighting the need for Web Application and API Protection (WAAP), which can comprehensively protect API security areas that traditional WAF alone lacks.
In order to meet this market shift, the security industry sees existing WAF vendors extending their existing web application firewall capabilities to add API protection,
Through the launch of a module type, we provide a Web Application and API Protection (WAAP) solution by expanding our product and service area, such as linking with existing products.
In other words, WAAP is not a completely new solution, but an addition or extension of API security features specialized in existing WAF solutions.
When searching for API security threats, the typical keywords that appear are "authentication", "authorization", and "authorization".
The underlying cause of API security threats is that visibility and complete management of numerous API End-Points is practically impossible, and every time a new API End-Point is created or modified, proper authentication and authorization is not achieved.
An example of a typical API security threat in which traditional WAF solutions are difficult to respond to (in other words, WAAP solutions respond) means that "BOLA" users bypass access permissions to data objects through APIs.
This allows attackers to access or manipulate unprotected data.
To illustrate an example of the BOLA attack, we look at two scenarios.
Examples of typical API security threats BOLA attacks
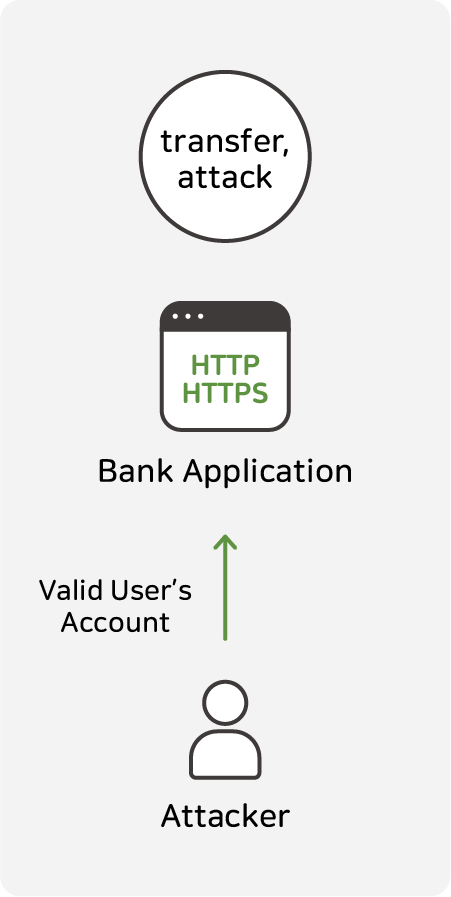
- Misuse of account rights: For example, in a banking application, customers can look up information about their accounts and make transfers. However, an attacker can log in as an authenticated user, access other customers' accounts through API, and attempt to transfer. This allows an attacker to exploit unrestricted authority to attack the system and perform abnormal actions.
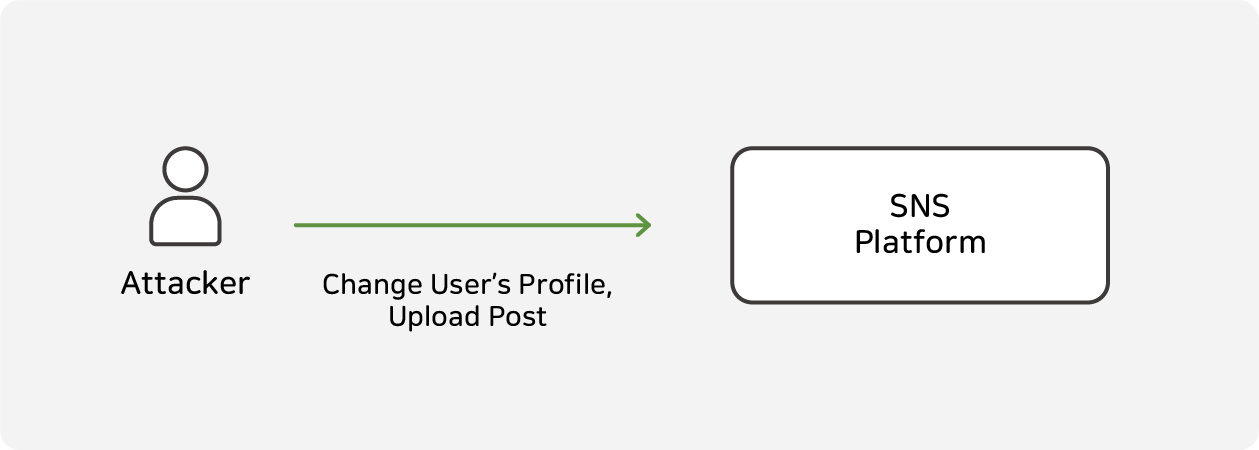
- Data Manipulation: On social media platforms, users can modify their profiles and create posts. However, the API allows an attacker to manipulate a user's profile to change another user's profile image, or to post posts that the user did not create.This can lead to confusion among users and problems such as spreading false information.
As seen in the above example, API security threats are primarily caused by flaws in terms of authority and role management, data integrity, and so on. Therefore, WAAP specialized in API security is needed to enhance this aspect and to ensure proper access control and data verification.
WAAP Solution Required
- Increasing Web Applications and APIs: Modern software development is increasingly moving around web-based and API-driven. These trends are related to the proliferation of cloud computing, mobile applications, IoT (IoT), and microservice architectures. As a result, web applications and APIs play a key role in many organizations, and the security of these systems is critical.
- Increasing security threats: Web applications and APIs are very useful targets for hackers.
Attacks such as SQL Injection, Cross-Site Scripting (XSS), authentication and session management issues, and API specification tampering can pose serious security threats. Such attacks can have serious consequences such as data exposure, service interruption, and compromise on customer trust in an organization. - Compliance and data protection: Many industries have introduced regulations that enforce the security of web applications and APIs. For example, the financial services industry must comply with regulations such as PCI Data Security Standards (PCI DSS) and General Data Protection Regulations (GDPR).These regulations emphasize web application and API security to enhance data protection and customer privacy
![]()


- Ensuring business continuity: Attacks and data exposure caused by security issues in web applications and APIs can have a direct impact on business continuity. Disruption of service, data leakage, and customer confidence can affect the reliability and reputation of your organization.WAAP ensures business continuity by enhancing the security of web applications and APIs.
Web Application Firewall (WAF) and WAAP (Web Application and API Protection) are both tools to enhance web applications and API security.
However, there are some important differences between the two solutions.
WAF vs WAAP
Scope and function:
- WAF: It focuses primarily on detecting and blocking attacks occurring in web applications.It operates primarily on the OSI layer 7 (Layer 7) of web applications and monitors HTTP and HTTPS traffic. Its main functions include detecting and blocking attacks such as SQL Injection, Cross-Site Scripting (XSS), authentication, and session management.
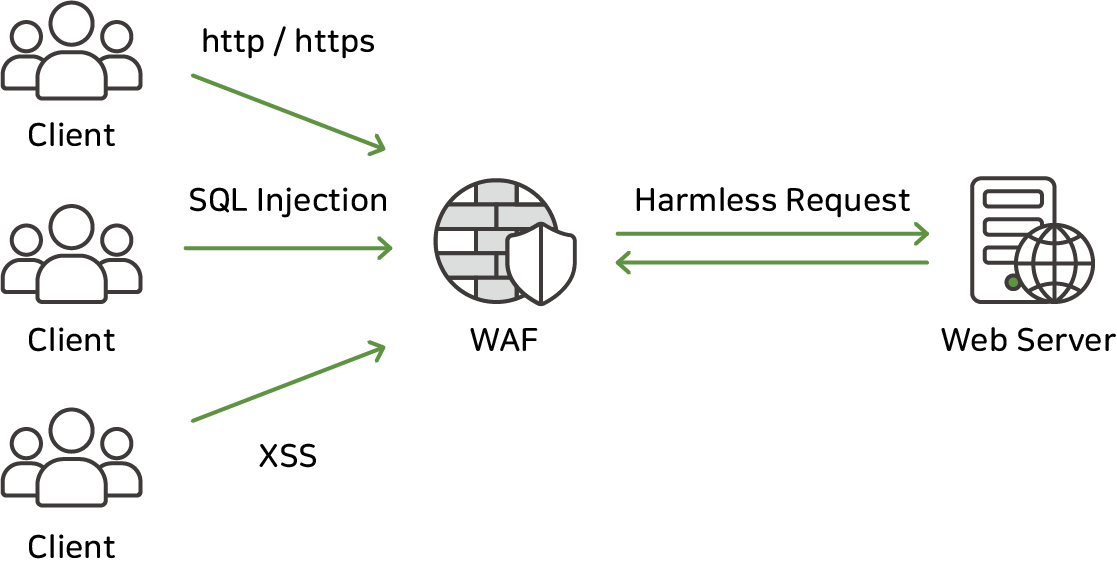
- WAAP: Provides a wider range of protection, including the capabilities of the WAF. WAAP protects APIs as well as web applications. This is important because APIs play an important role in mobile apps, IoT devices, and applications that interact with other clients.WAAP also detects and prevents attacks on API endpoints.
API Protection:
- WAF: API protection lacks special features; WAF may not be efficient when dealing with APIs.APIs typically use other protocols, such as REST or GraphQL, which can be complicated for WAF to handle by default.
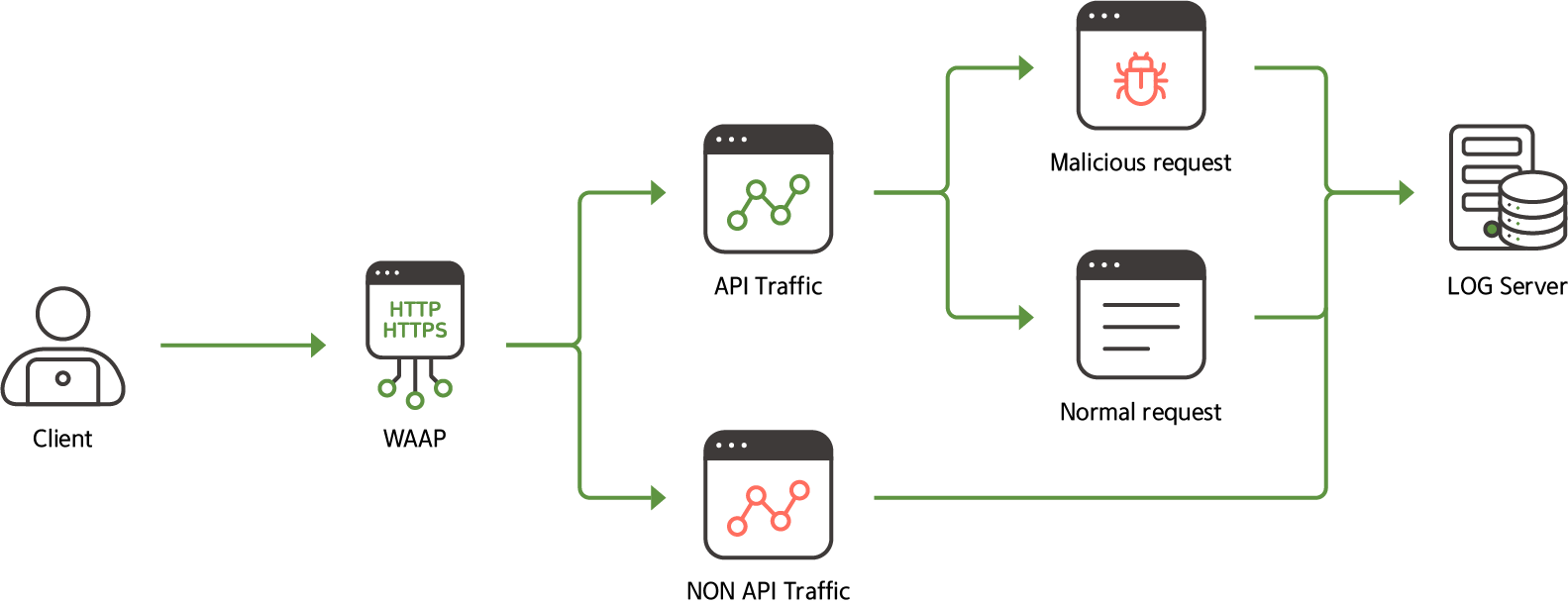
- WAAP: API protection is one of the key functions of WAAP. WAAP provides the ability to monitor the API's traffic and identify and prevent API specific attack patterns.
To be operated:
- WAF: It is mainly used and managed by web security experts. Most of the time, a security expert from web applications is required.
- WAAP: You need more specialized security techniques compared to WAF. You need an understanding of API protection and management, and you may need the knowledge of some API security experts.
WAAP is generally divided into an appliance (APPLIANCE) type and a subscription security-as-a-service type, In addition to web application security and API security, we focus on Bot mitigation and DDoS mitigation.
However, for the appliance type, the corresponding area for DDoS is Layer 7 HTTP(S),Subscription security service types vary with network and HTTP(S) DDoS across Layer 3 through 7.
APPLIANCE:
The appliance is installed directly on the internal network, allowing you to monitor and process traffic within the network in real time.
This can provide faster response and lower latency, and because it is directly integrated into the organization's internal infrastructure, it provides overall control over security.
In addition, the appliance type provides a wealth of setup options for users to customize their security policies.
This helps you build security solutions tailored to your organization's unique needs.
The initial purchase, maintenance costs for hardware purchase and maintenance are high, and the performance of each model/lineup is limited in scalability, such as the need for additional equipment to handle large-scale traffic.
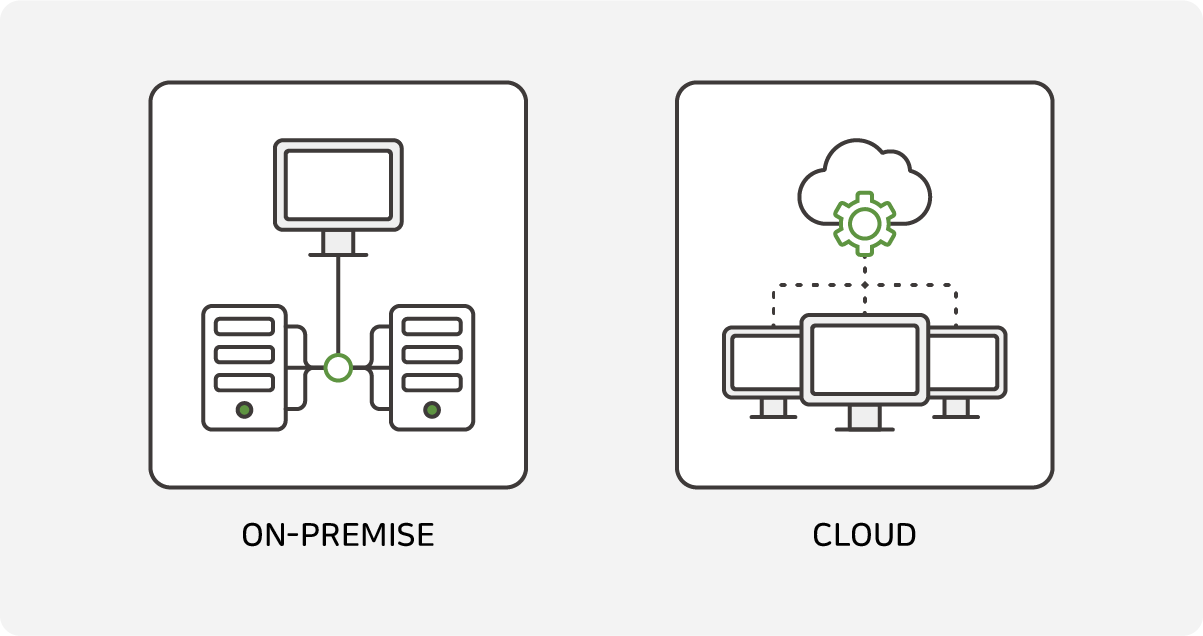
Security-as-a-Service:
Subscription services are available out-of-the-box without the need for special hardware purchases or installations, so initial investment and maintenance costs are low.
Usually, you can subscribe immediately if you pay only a monthly or annual subscription fee, and if the service is deemed inappropriate, you can easily cancel it.
In addition, cloud-based services can easily expand traffic processing capabilities as needed.
Unlike appliances, cloud-based services do not have direct access to internal infrastructure, which limits the customization or control of some of the security policies.
Taking these advantages and disadvantages into account, it is important to select the type that best suits each organization's needs and operating environment.
MONITORAPP is a WAAP solution vendor (or service provider) covering both On-premise and Cloud, from APPLIANCE type AIWAF, Virtual APPLIANCE type AIWAF-VE,
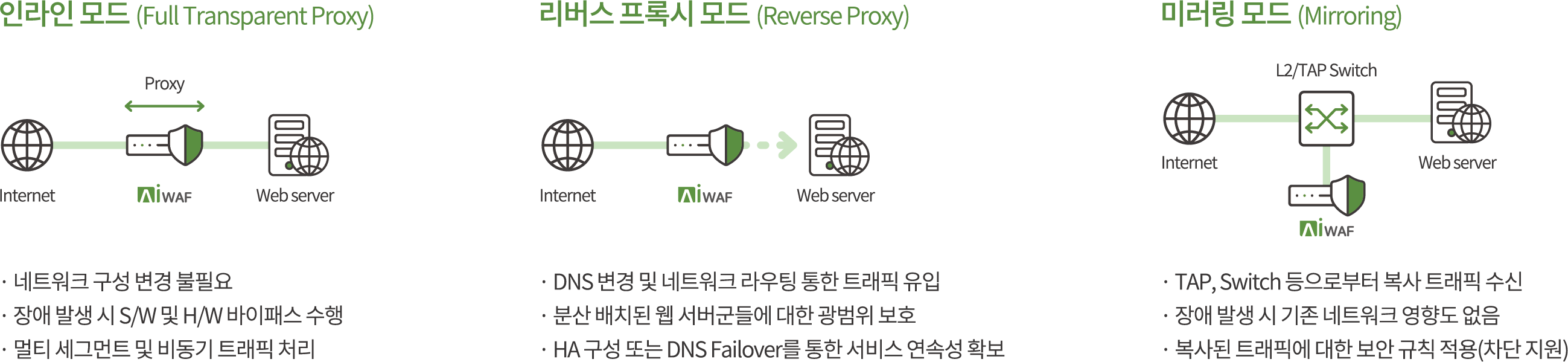
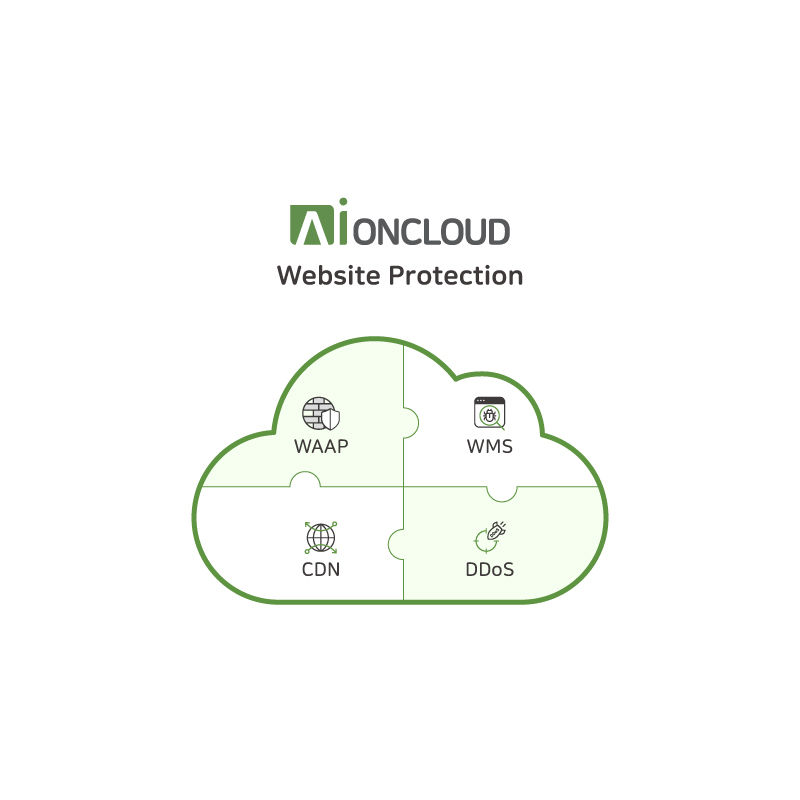
and cloud-based subscription security service type AIONCLOUD WAAP,
see https://www.monitorapp.com and https://www.aioncloud.com for more information.