Monitorapp Threat analysis Myunghoon Chea With the spread of COVID-19, changes have been happening in society, including work, education, and even social life. As the usage of video meeting programs is increasing in companies and schools, the attempts from cyber attackers targeting vulnerabilities of video meeting programs have been increasing rapidly. Thus, we look at the security measures that users can take when using such programs.
|
- Zoom Bombing
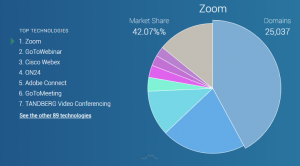
Source: https://www.datanyze.com/market-share/web-conferencing–52
There have been increasing reports on vulnerabilities regarding Zoom, which is the world’s largest video conferencing company. Zoom is used in various industries and increasingly so due to the COVID-19 pandemic.
A new term, named “Zoom Bombing,” was named after the software. “Zoom Bombing” refers to any action that interrupts the video call in any way. The attackers can disrupt the meeting by displaying lewd images, shouting profanities, etc. They also yell racial, sexual, or religious slurs along with displaying violent images. Although the term “Zoom Bombing” originated from Zoom software usage, it now refers to any attacks on various video chatting platforms.
The reason that “Zoom Bombing” became a popular term is that the attacks using Zoom’s lack of participant authentication became popular worldwide. In general, when an invitation is made to a video participant, an invitation with a link is sent. The invitee can join the meeting by clicking the link. At this time, if the meeting organizer set the conference room without setting a password, joining the room is possible without additional authentication. With the link address, a third party can enter the meeting and intrude. Until recently March, a person could have joined a conference with just an ID and no additional authentication. However, from the 5th of April Zoom made it a default setting to set up a password for a conference ( https://support.zoom.us/hc/en-us/articles/360041408732 ).
As COVID-19 became prevalent around the world, the usage of Zoom software skyrocketed. As a result, the ID addresses (links) were shared on places like social media sites and the attackers were able to acquire them by searching them on search engines or from social media sites or intrude on a conference call using brute force attack.
Also, various security issues are being raised on the Zoom platform, such as the possibility of sensitive information leakage due to end-to-end weak encryption (AES-128), encryption/decryption key via a specific country server, and leakage of personal information of iOS app ( https://www.cnet.com/news/zoom-security-issues-zoom-could-be-vulnerable-to-foreign-surveillance-intel-report-says/ ).
- Video Call Apps
The security issue of video conferencing is not limited to a specific platform since a higher market share can mean higher usage, which can uncover more security issues. The following is a list of software that meets the ‘minimum security standard’ in the recent ‘Video Conference Platform Security Check’ conducted by Mozilla (https://foundation.mozilla.org/en/privacynotincluded/categories/video-call-apps/ ).
- Zoom ( Zoom)
- Hangout ( Google )
- FaceTime (Apple)
- Skype ( Microsoft )
- Facebook Messenger ( Facebook )
- WhatsApp ( Facebook )
- Houseparty ( Epic Games)
- Discord ( Discord )
- Jitsi Meet ( 8×8 )
- Signal ( Signal Tech )
- Teams ( Microsoft )
- BlueJeans ( Verizon )
- GoToMeeting ( LogMeIn )
- Webex ( Cisco )
- me ( Doxy.me )
Video conference software cannot be perfect, like any other software, so having a solid security practice in place is necessary for the users.
- security measures
- Maintaining updated software and OS
All software may have security vulnerabilities, and if a vulnerability is reported, it is usually patched quickly so always keep the software version up to date to respond to known vulnerabilities. One of the most important steps in information security is to keep the software and OS up to date.
- Conference ID protection
As mentioned earlier, the “Zoom Bombing” attack relies on a conference that is not password protected. People often post their meeting IDs (addresses) online, such as on social media, to become self-proclaimed targets of attackers. Therefore, posting a meeting ID (address) online is discouraged. Also, a password should be set for any video conference call.
- Use the waiting room feature
Most video conferencing software supports a ‘waiting room’ function. Participants will not be able to enter the meeting right away but will enter a kind of ‘waiting’ space, and the meeting organizer will select the people who are allowed to enter the meeting to prevent uninvited participants from entering.
- Beware of phishing
Always be vigilant when clicking on the invitation link for a meeting. You should always be cautious about meeting invitation sent from anonymous users. You should also be careful about link access in chat rooms during a video conference. Some attacks will impersonate as a meeting invitation link and send the address of a malicious site, inducing it to download malware or enter personal information.
Due to the prolonged pandemic, work-from-home and video conferences are projected to increase in its usage. Looking at vulnerabilities discovered so far, attacks on video/online chats are predicted to increase in the future. Each user should be vigilant and abide by the security guidelines provided by the official sources.