Hello, We are MONITORAPP, a company specializing in application security.
Zero Trust Network Access (ZTNA), commonly known as a replacement technology for VPNs,
actually provides other useful functions for security administrators in addition to basic functions.
Today, let's take a look at some of the additional features that security administrators can take advantage of.
Restrict access to pre-registered devices only


Previously, if the user who connects mainly with a combination of ID/PW was authenticated,
it is also a method of authenticating the connected device.
It is true that ID/PW has been useful as a means of authentication for a very long time,
but now there is a widespread perception that this alone is no longer a valid means of authentication.
This is because authentication information can be leaked through phishing, etc., or
it can be neutralized by malicious attacks such as random college admissions or credential stuffing.
To this end, as a method of Multi Factor Authentication (MFA),
there is a way to allow authentication only in pre-registered devices such as laptops paid by the company.
This is a technology that does not allow authentication even if the ID/PW is correctly entered on other devices.
It is similar to setting up a device that is allowed when logging into OTT or bank sites,
mainly by installing specific certificates on the device or by using unique UUID information for each device.
"Device Posture" to check the status of the device


If the aforementioned feature is hardware-based "device authentication,"
it checks various features of the OS in the device to determine whether to allow access or not.
This means that you should check the type and version of the OS installed, set the score for each item based on criteria such as the degree of OS security patches,
whether a specific anti-virus program is installed and running, or whether a specific file is in a specific path to allow access.
Of course, if you don't meet certain requirements, you can deny access at all.
In particular, this function is also related to "Continuous Authentication," which is discussed in Zero Trust.
This does not mean that you simply authenticate multiple times,
but even if you pass certification, if you do not meet the criteria through continuous status checks,
you can cut off access, block, or induce recertification even after certification.
For example, at the time of authentication, the anti-virus program worked and passed the authentication,
but if you arbitrarily turn off the program after authentication, you will be able to invalidate the authentication.
User will not be allowed to arbitrarily ZTNA Off
I don't know if it's an in-house where your traffic can be monitored and controlled,
If you use the Internet using a laptop at a remote location such as a business trip or a cafe,
there is a limitation that you cannot control it unless you access an existing VPN and do a backhaul through the in-house network.
As a security manager, if you always want to apply the same security policy regardless of the user's location, all traffic should go through the SSE platform.
This requires a function that prevents the user from arbitrarily turning off the ZTNA agent.
This means that when the OS is booted, the ZTNA agent automatically operates,
and if the ZTNA agent is not activated through authentication, users cannot use the Internet at all.
This feature is policy-oriented and allows the administrator to control whether the console enforces its settings for all users or gives you the option of On/Off for a particular user or group.
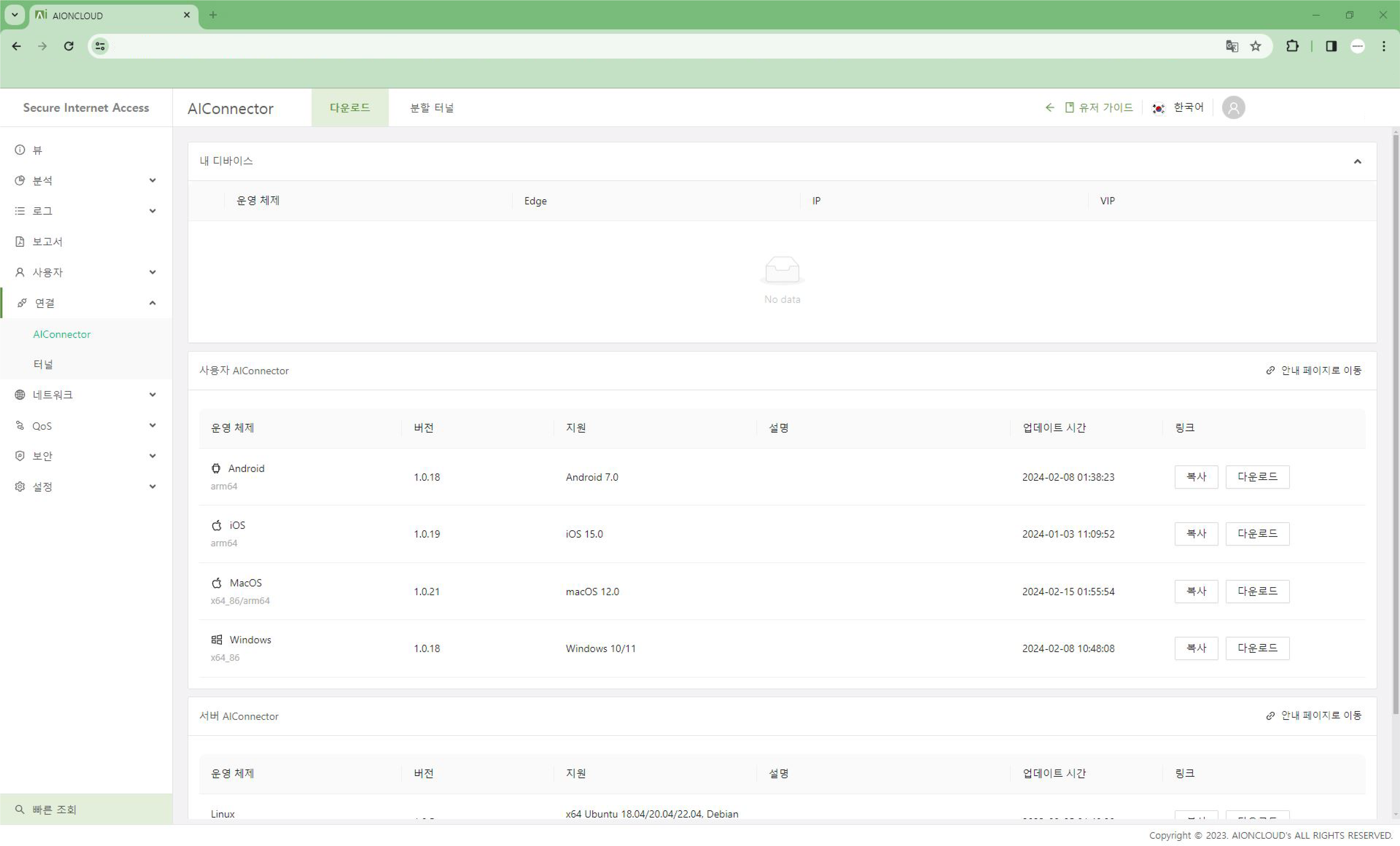
So far, we've looked at some of the additional features of ZTNA. I've mentioned that it's an additional feature,
but it's actually a very important element, so it can be a very useful security feature if you use it well from the perspective of a security administrator.