Fast, secure, seamless access to private applications
Application Insight
Zero Trust Network Access
Zero Trust Network Access
AIZTNA offers a secure access environment for users connecting to
private apps ensuring fast and direct application connectivity.
Product Lineup

AIZTNA
Physical appliance type
AIONCLOUD ZTNA
Cloud-based platforms
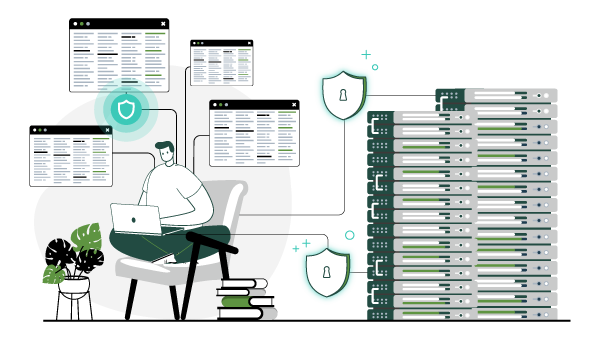
Create a secure remote access experience with zero-trust-based network access
Product Overview
MONTIORAPP’s ZTNA
Goes beyond legacy network security measures
MONITORAPP’s ZTNA solution verifies user identity and device context
for every enterprise application access request, ensuring that only
authorized users and devices can connect with the least privilege. By
leveraging the SDP framework, it fully safeguards corporate resources
and delivers robust access control, eliminating security threats
associated with traditional network-level VPN connections through
application-level access.
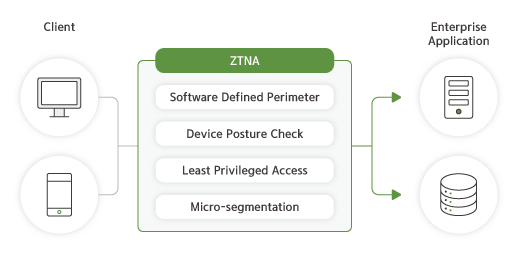
Product Features
Provide a secure connection experience.
Software Defined Perimeter
Minimizes the visibility of the corporate network to ensure
protection from external threats, preventing the network from being
exposed.
Device Posture Check
Evaluates the security posture of devices attempting to access
corporate applications in real-time, allowing only authorized
devices to connect.
Least Privileged Access
Grants users only the least privileged access necessary for their
work, restricting access to unnecessary data.
Micro-segmentation
Enforces application-centric access control, allowing access only to
authorized individual applications.
Replacing legacy network access solution
Continuous trust verification
Continuous device posture evaluation and monitoring
Least-privileged access to reduce the attack surface
Application-centric access control
Zero Trust based Secure Access
The Zero Trust Principle, "Never Trust, Always Verify," forms
the foundation for strictly managing all network access. It does
not assume the reliability of users or devices in advance.
Instead, every access request undergoes rigorous authentication
and verification to safeguard sensitive corporate data and
applications. This approach effectively blocks potential
internal and external threats, making it difficult for attackers
to gain access to the corporate network.


Enhanced Security Posture
AIZTNA, built on a Software Defined Perimeter (SDP) framework,
controls access based on user identity and connection context.
This minimizes the visibility of the corporate network,
protecting it from external threats and preventing exposure to
the outside. Users must meet strict identity verification and
access conditions to connect to corporate resources. This robust
access control further strengthens the security perimeter of the
corporate network.
Device Posture Check
AIZTNA’s Device Posture Check evaluates the security status of
devices attempting to access corporate applications in
real-time, allowing access only to authorized devices. It
verifies OS patch levels, antivirus software presence, process
names, and more, blocking devices that fail to meet security
requirements. This ensures safe access in BYOD (Bring Your Own
Device) environments, effectively managing the security posture
of all connected devices and enhancing overall organizational
security.


The Least Privileged Access
Aligned with the principle of least privilege, users are granted
only the minimum access permissions necessary for their tasks,
while unnecessary data access is restricted. Real-time access
management ensures that unauthorized users cannot access
sensitive information, with granular access controls customized
for each department and user role.
User-to-App Segmentation
AIZTNA provides granular access management to corporate
applications, granting access only to necessary applications
based on user privileges. This prevents unnecessary lateral
movement within the network and mitigates security threats. In
the event of a breach, it prevents the spread to other areas,
thereby strengthening internal security and protecting sensitive
corporate applications.

X