Hello, this is MONITORAPP.
MONITORAPP operates AILabs, a cyber threat intelligence platform developed in-house.
In our last post, we introduced what AILabs is,
Today, I'd like to take it a step further and explain how AILabs is utilized in various products and services at MONITORAPP.
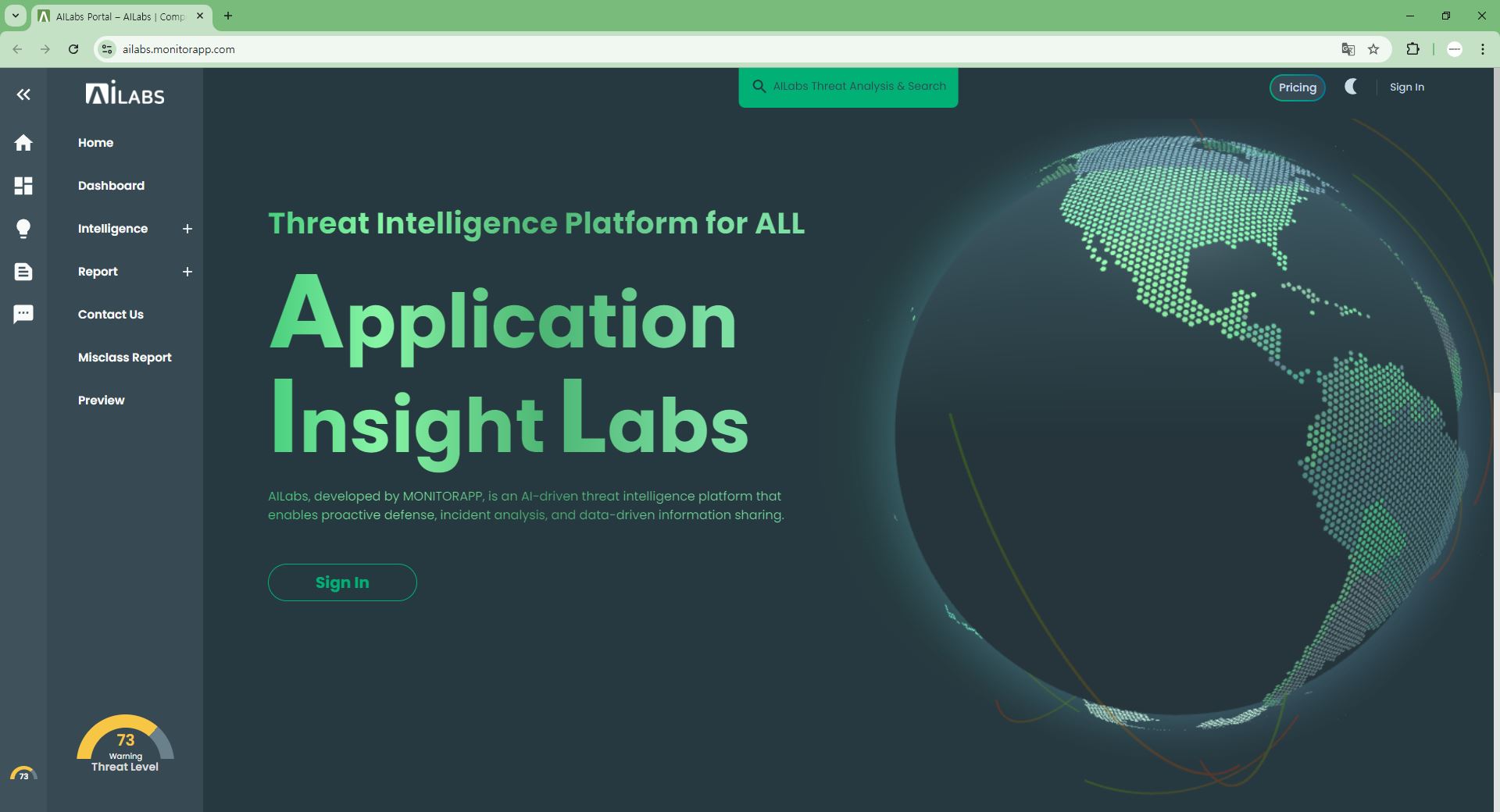
AILabs is a four-step process consisting of Collection, Analysis, Processing, and Distribution.
to provide the insights needed to protect your organization's assets.
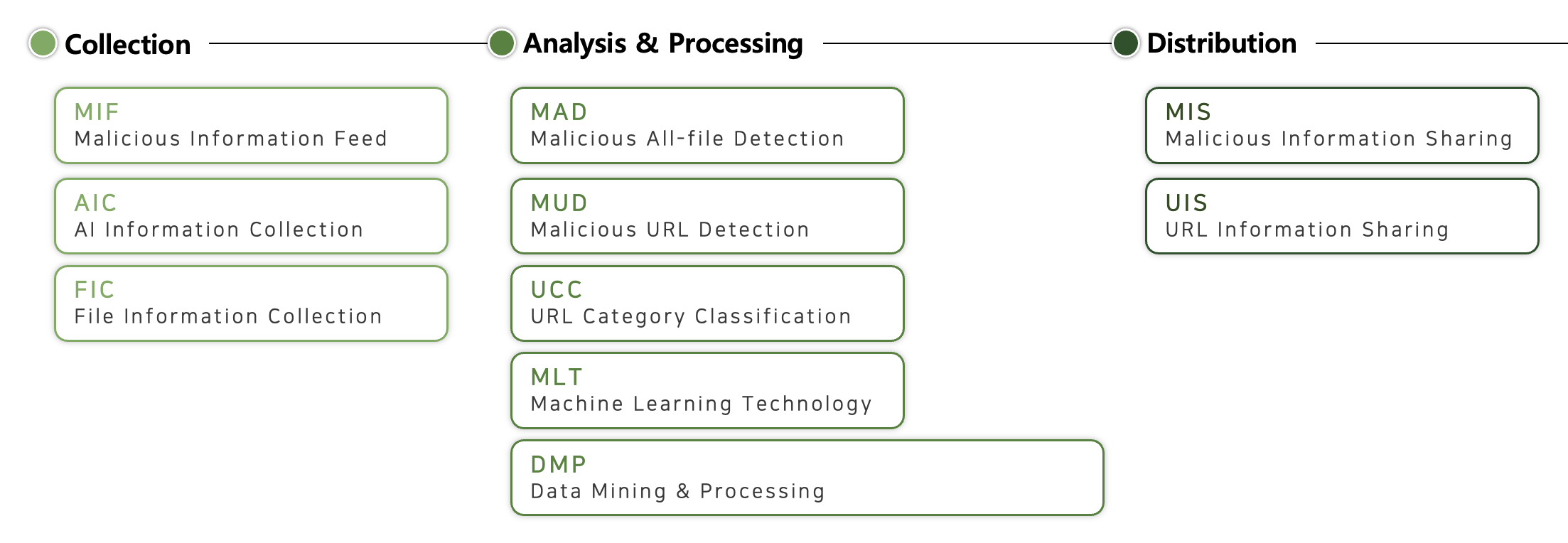
Today, we're going to introduce you to a few of these systems, representing the Collection, Analysis, and Processing phases.
Collection
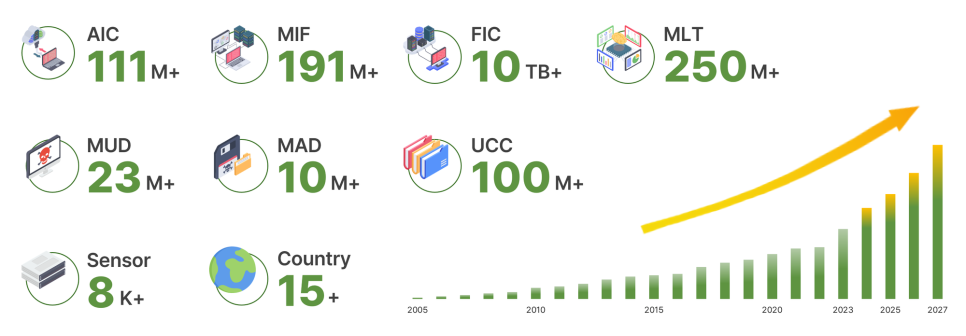
MIF(Malicious Information Feed)
MIF is a malicious information gathering system in which intelligent crawler agents periodically visit various channels to collect various unstructured threat data.
It also collects data in connection with the Korea Internet & Security Agency C-TAS and MISPs, and utilizes the Korea Communications Commission's harmful site URL information.
The data collected from various aspects is stored in the big data DB of 'AILabs' after standardization work including type classification, and is used for malicious URL detection and analysis.
FIC(File Information Collection)
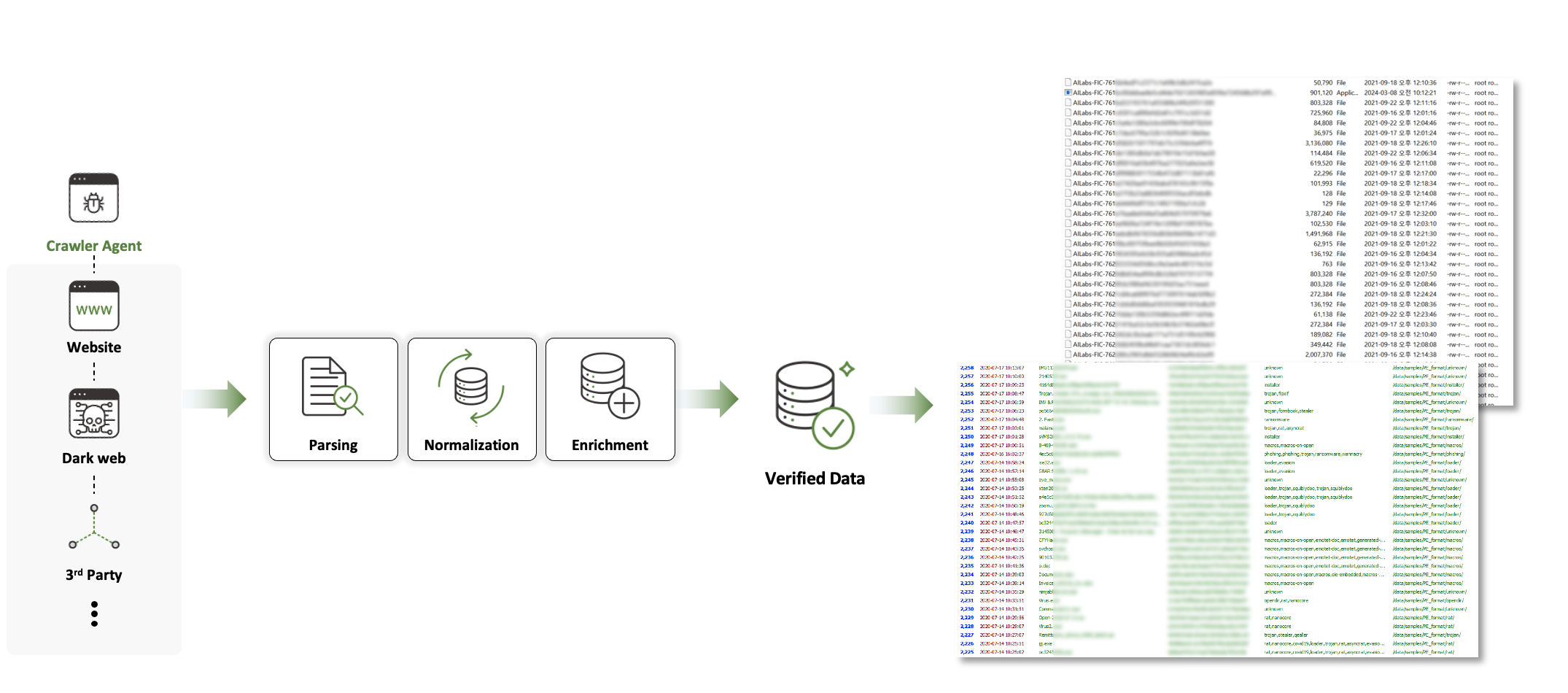
FIC is a malicious file information collection system where intelligent crawler agents periodically utilize various channels to collect various malicious files, refine and standardize malicious file type information, and then use it.
The collected data is stored in the big data DB of 'AILabs' after standardization work including type classification, and is used as machine learning learning data and utilized for malicious file detection analysis (MAD).
Analysis & Processing
MUD(Malicious URL Detection)
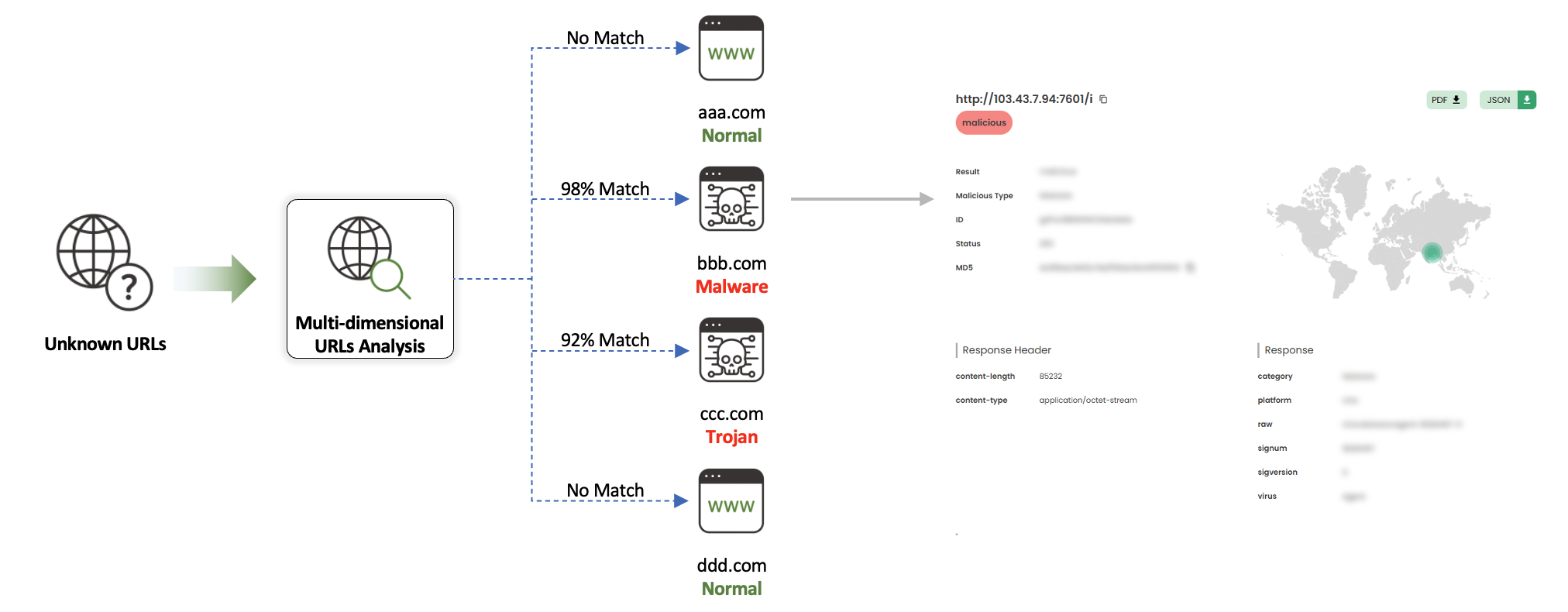
MUD is a system that detects malicious URLs by performing a multidimensional analysis of URLs.
It utilizes data collected by MIF, as well as static and dynamic analysis of website response data and downloaded files, feature data extraction, and machine learning prediction, and further performs precise identification based on various threat categories such as Trojan, Malware, Dropper, Exploit, and Ransomware.
MAD(Malicious All-file Detection)
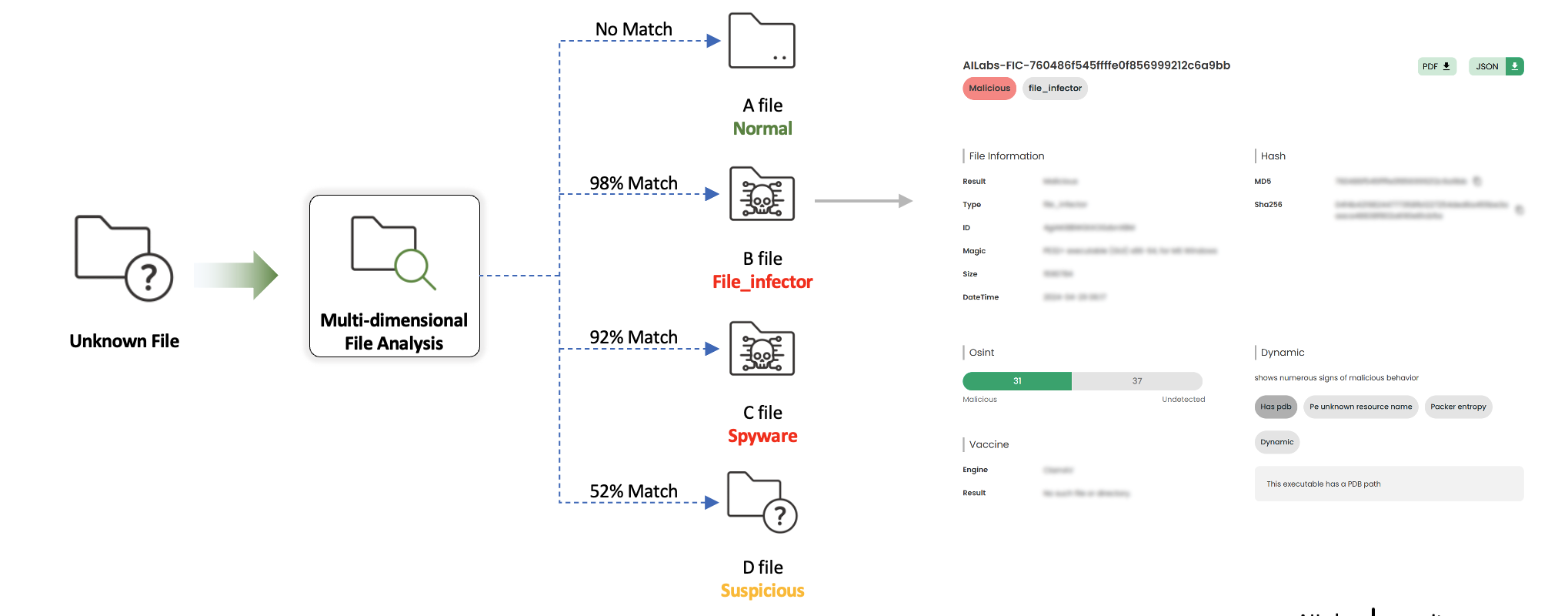
MAD is a system that uses multidimensional analysis to comprehensively analyze files to detect malicious files.
In addition to utilizing the data collected by FIC described above, it also utilizes multi-dimensional methods such as static/dynamic analysis, feature data extraction, machine learning prediction, OSINT reputation lookup, third-party integration, and antivirus, and performs precise identification based on various threat categories such as file injector, spyware, adware, worm, packed, etc.
It also integrates with VirusTotal, MITRE Att&ck, UARA-AlienVault Signature, MISP, and performs similarity analysis using previously analyzed malware profile information.
UCC(URL Category Classification)
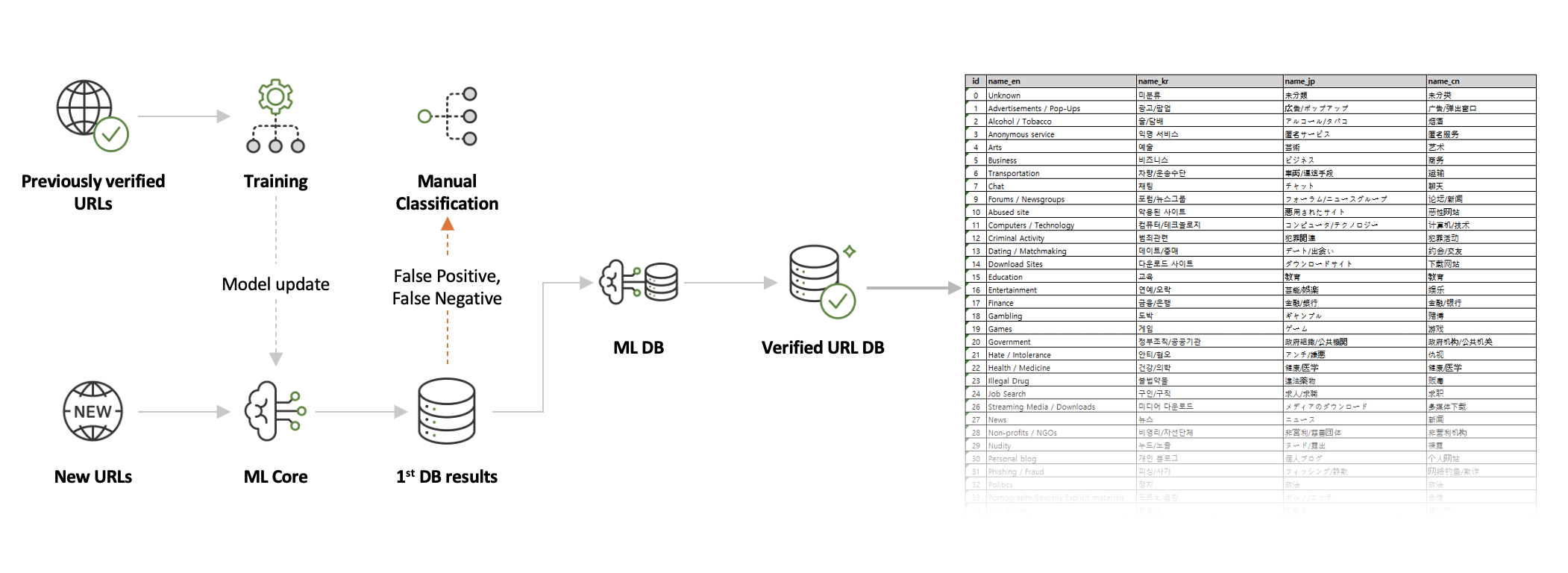
UCC is a system that categorizes and manages URLs by assigning them categories based on their characteristics.
UCC uses a machine learning algorithm based on morphological analysis to automatically classify URLs into categories, and the categories are optimized to meet global standards.
In addition, AILabs provides country-specific IP information, Black IP information, C&C IP information, and application/protocol-related information to be utilized in various products and services of MONITORAPP, as well as independent 'AILabs Portal' and 'AILabs API'.
MONITORAPP's security products go beyond traditional security solutions and work in conjunction with our CTI platform, AILabs, to effectively close security holes in response to rapidly evolving modern cyberattacks.
Protect your valuable assets with AILabs, which is continuously evolving as you read this, and with MONITORAPP's various products and services in conjunction with AILabs.
To learn more about 'AILabs', please visit
https://ailabs.monitorapp.com/
Please refer to the URL above.
In the next post, we will discuss the Distribution of 'AILabs'.
Thank you.