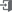Hello, this is MONITORAPP.
As we enter the digital age, the security needs of organizations are rapidly increasing.
Zero Trust Network Access (ZTNA) is an approach designed to meet these needs, providing enhanced security while ensuring user convenience.
Zero Trust Architecture (ZTA) continuously validates all users and devices and enhances data protection.
The core components of ZTA include Micro-Segmentation, Enhanced Authentication, and Software-Defined Perimeter.
Last time we talked about Micro-Segmentation,
today we're going to talk about the second, Enhanced Authentication.
Traditional authentication methods
Traditional authentication methods primarily rely on single-factor authentication (SFA) to verify a user's identity.
The most common form of SFA is a username and password combination.
SFAs are less secure and can easily lead to unauthorized access if the password is compromised or guessed.
Additionally, if you need to use different passwords for different systems, you'll have to remember them all, which degrades the user experience.
Traditional authentication methods are fixed, applying the same authentication process for every access attempt.
This makes it inflexible and difficult to respond to different threat scenarios.
'Enhanced Authentication' in ZTNA
ZTNA introduces an additional layer of security beyond a simple username and password to continuously verify a user's identity.
This is based on Zero Trust principles, and the main components of 'enhanced authentication' are
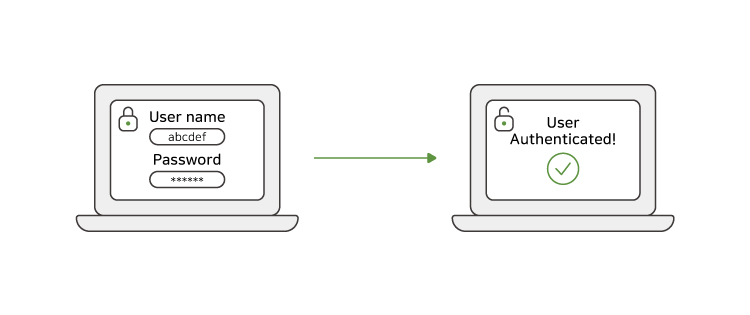
1. Multi-factor authentication (MFA)
Verify a user's identity using two or more authentication factors, such as a password, biometrics, or a one-time password (OTP).
MFA provides an additional layer of security to prevent unauthorized access even if one authentication factor is compromised.
For example, if your username and password are compromised, you can still prevent unauthorized access by entering your OTP.
2. Context-aware authentication
Detect anomalies by analyzing information such as the user's connection location, device status, and connection time,
and require additional authentication if necessary.
This adds another level of security.
3. Continuous monitoring and evaluation
We continuously monitor and evaluate user behavior to detect unusual activity.
This allows us to block threats in real time.
How IDaaS and SSO came to be
When it comes to implementing enhanced authentication, it's not enough to simply add multiple layers of security.
You also need an efficient approach that takes the user experience into account.
This is where single sign-on (SSO) and identity as a service (IDaaS) come into play.
SSO and IDaaS are concepts that were developed to make organizations more secure and efficient in the digital age.
Together with ZTNA, SSO and IDaaS significantly improve the security and manageability of organizations.
ZTNA is based on the principle of Zero Trust to continuously validate all access,
By utilizing SSO and IDaaS, you can achieve both enhanced security and user convenience.
What is SSO?
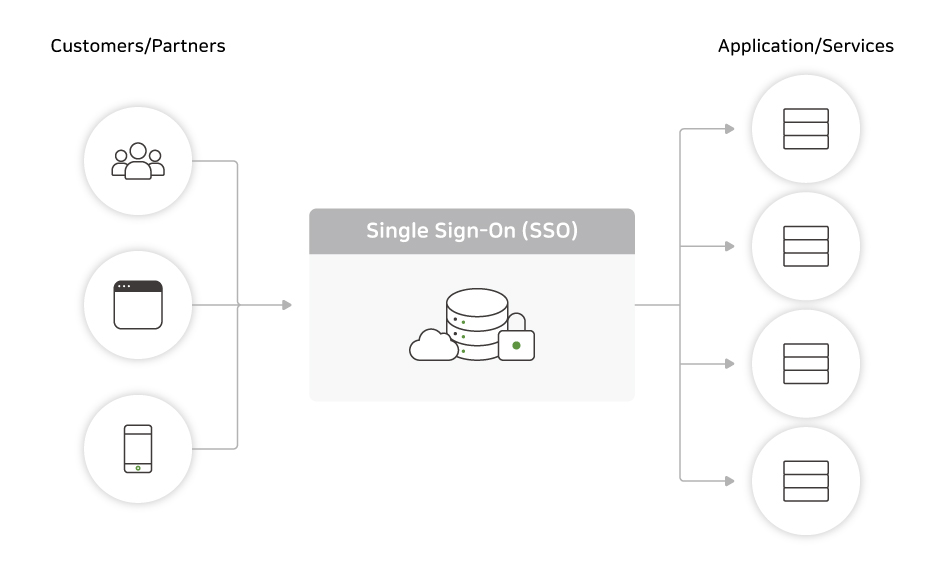
Single sign-on (SSO) is an authentication method that allows users to access multiple applications or systems with a single sign-in.
SSO helps reduce the burden of remembering multiple usernames and passwords, improves user experience, and increases security.
Benefits of SSO include convenience, increased security, and manageability.
What is IDaaS?
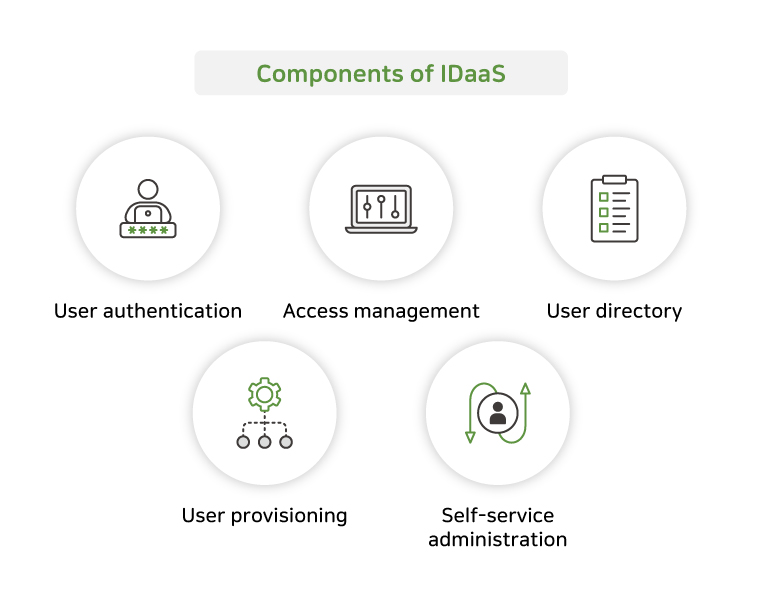
Identity as a service (IDaaS) is a cloud-based identity management solution that provides a range of identity and access management capabilities, including user authentication, authorization, directory services, and more.
Benefits of IDaaS include cost savings, scalability, increased security, and compliance.
Benefits of aligning ZTNA with SSO and IDaaS
By aligning ZTNA with SSO and IDaaS, your organization can benefit from the following
1. Enhanced security

Increase security with multi-factor authentication and context-aware authentication with MFA.
Prevent unauthorized access by continuously verifying a user's identity.
2. Centralized management

IDaaS allows you to centrally manage user accounts and access rights.
This greatly improves management efficiency.
3. Improve user experience

SSO allows users to seamlessly access multiple applications.
This greatly improves the user experience.
4. Regulatory compliance
IDaaS helps organizations meet regulatory requirements with audit logs and reporting capabilities.
5. Reduce costs
Cloud-based IDaaS saves you the cost of building your own infrastructure and is highly scalable, giving you the flexibility to grow with your organization.
ZTNA services such as AIONCLOUD's SRA provide enhanced security, user-friendliness, and manageability through 'hardened security'.
AIONCLOUD's SRA overcomes the limitations of traditional SFA by supporting MFA, and allows you to efficiently manage users without disrupting your existing environment with SSO and IDaaS.
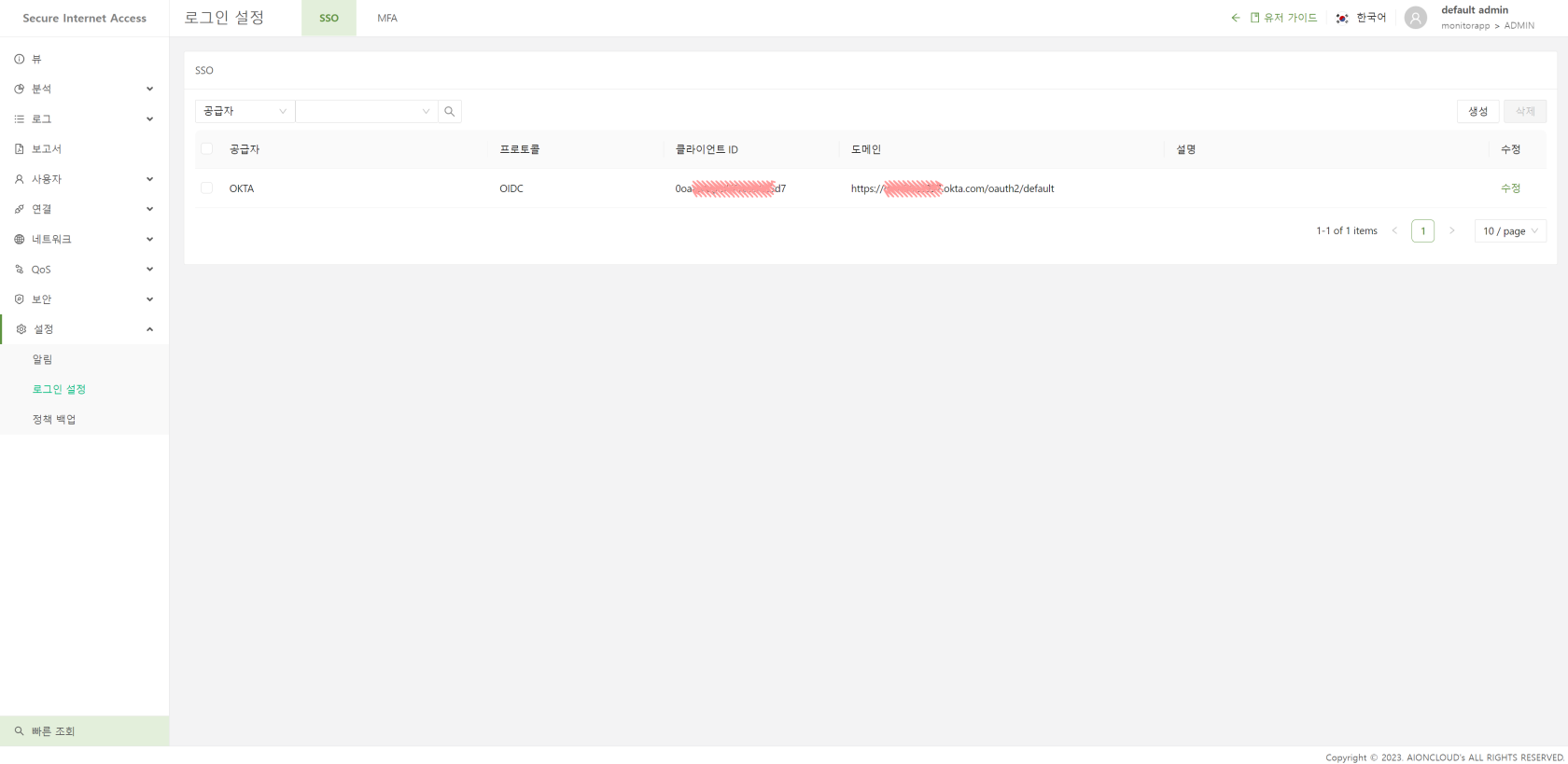
You can also set up MFA on a per-group and per-user basis, providing a stronger authentication scheme.
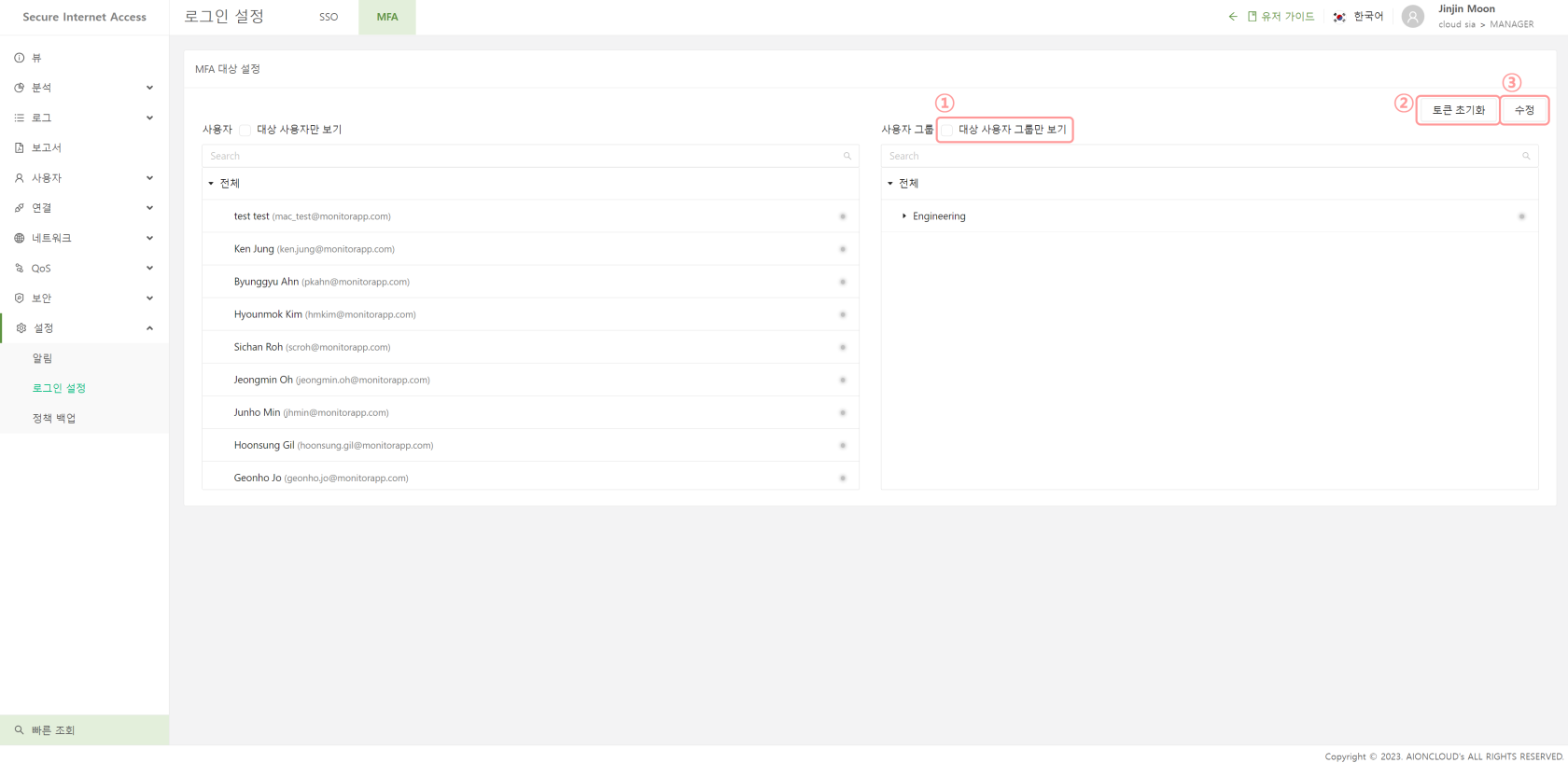
AIONCLOUD's SRA utilizes IDaaS and SSO to centrally manage user accounts and access rights, and policy settings can be made by user and group, enabling efficient policy settings and ZTNA service usage.
SSO and IDaaS play an important role in making organizations more secure and efficient in the modern IT environment.
SSO provides convenience for users, while IDaaS improves an organization's overall security posture through centralized management and enhanced security.
By leveraging IDaaS solutions like Okta and MS Entra ID, you can maintain your existing user authentication schemes while supporting SSO to create an efficient and secure authentication scheme.
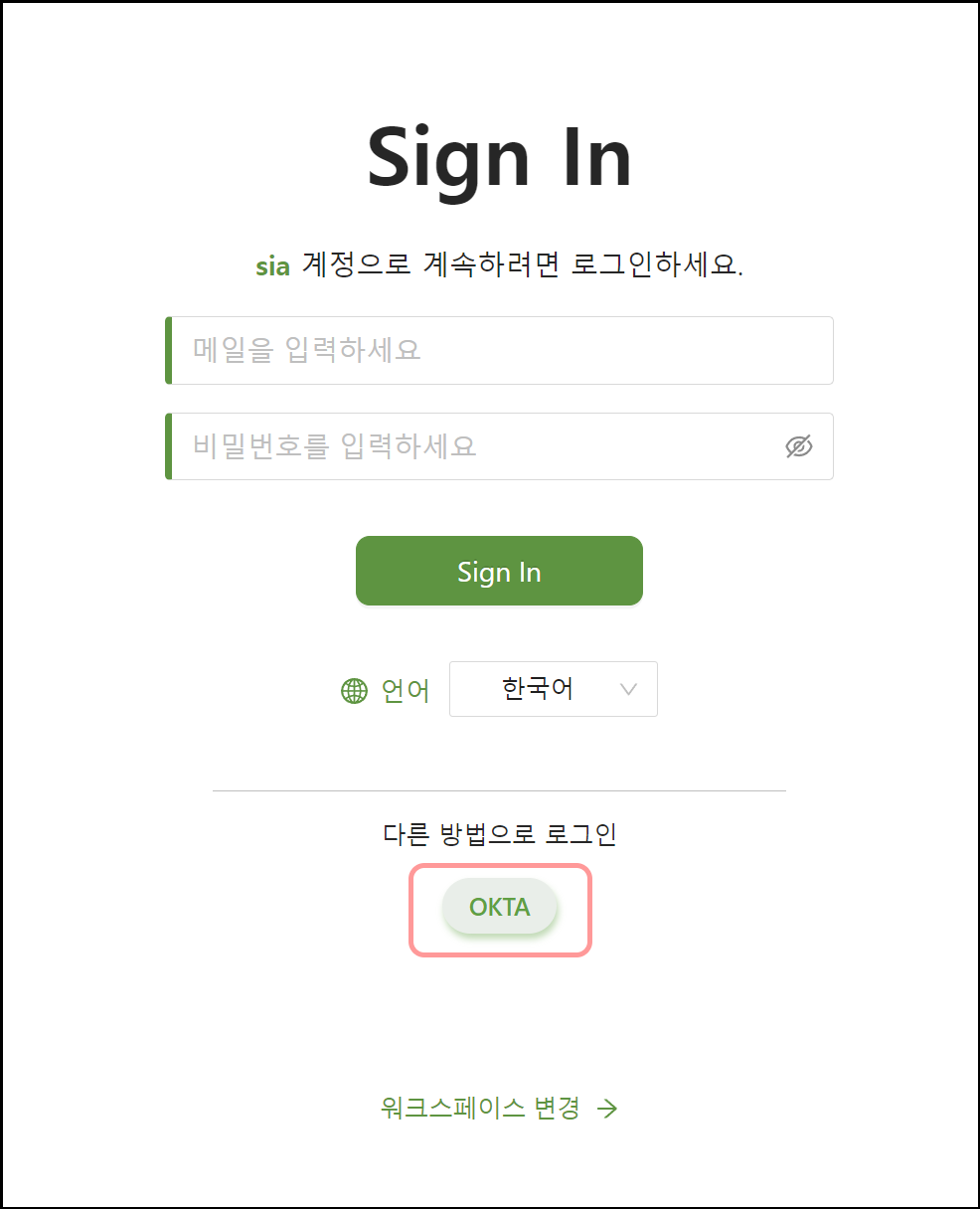
This unified approach strengthens an organization's security posture, improves user experience, and facilitates regulatory compliance.
Manage your organization's application access more securely and efficiently with AIONCLOUD SRA, which supports SSO, IDaaS, and enhanced authentication schemes with MFA.
For more information about AIONCLOUD SRA, please visit
https://www.aioncloud.com/secure-internet-access/
See the URL above.
We'll introduce the rest of SRA's features in our next post.
Thank you.