Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent. This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of August 2024.
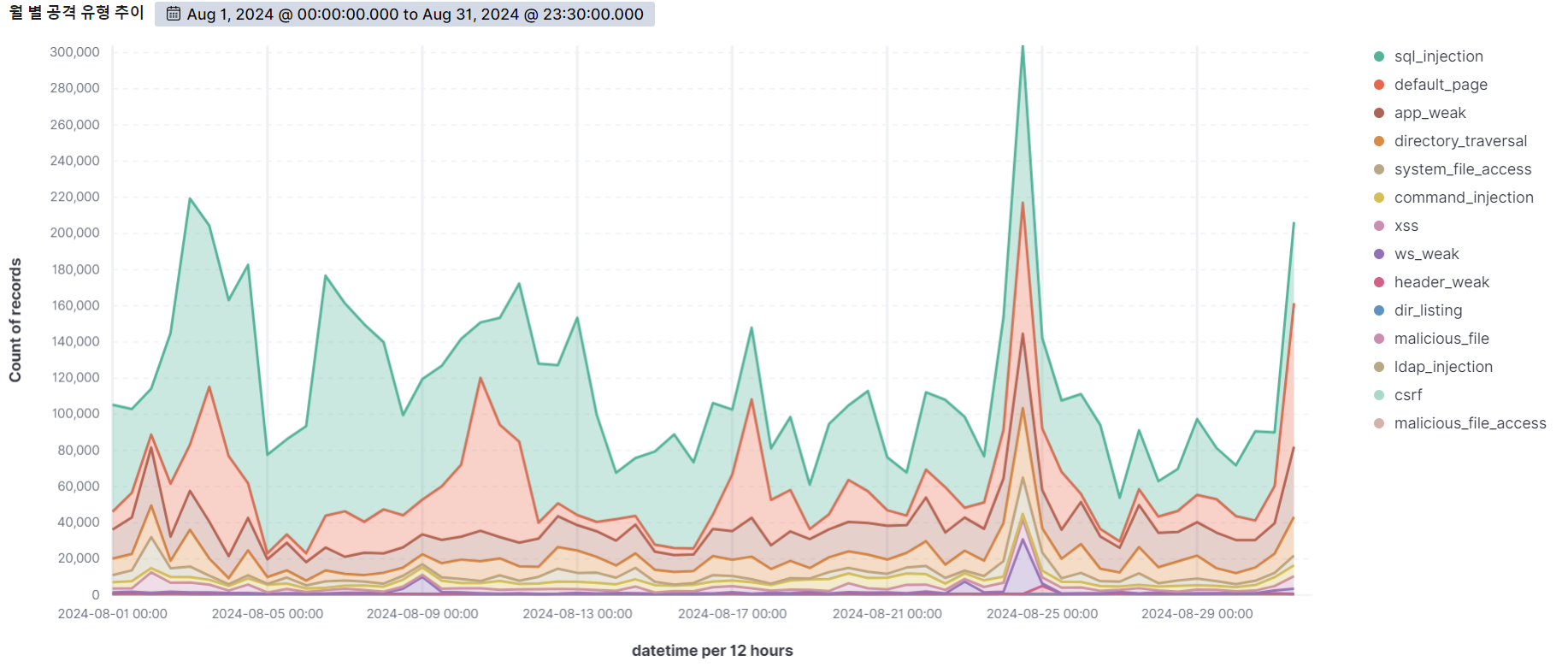
In August 2024, we detected over 240,000 attacks per day on average, with the highest number of attacks occurring on the 24th.
SQL Injection, the vulnerability with the most attempted attacks on the 24th, has the most detection conditions in our AIWAF. However, SQL Injection attacks are always being monitored because there are many new attack types and evasion methods.
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month. Based on this, you can establish basic web attack response guidelines to prevent and respond to these types of attacks.
The graph below shows the web attacks detected by AIWAF as of August 2024.
Web Attack Trends by Rule
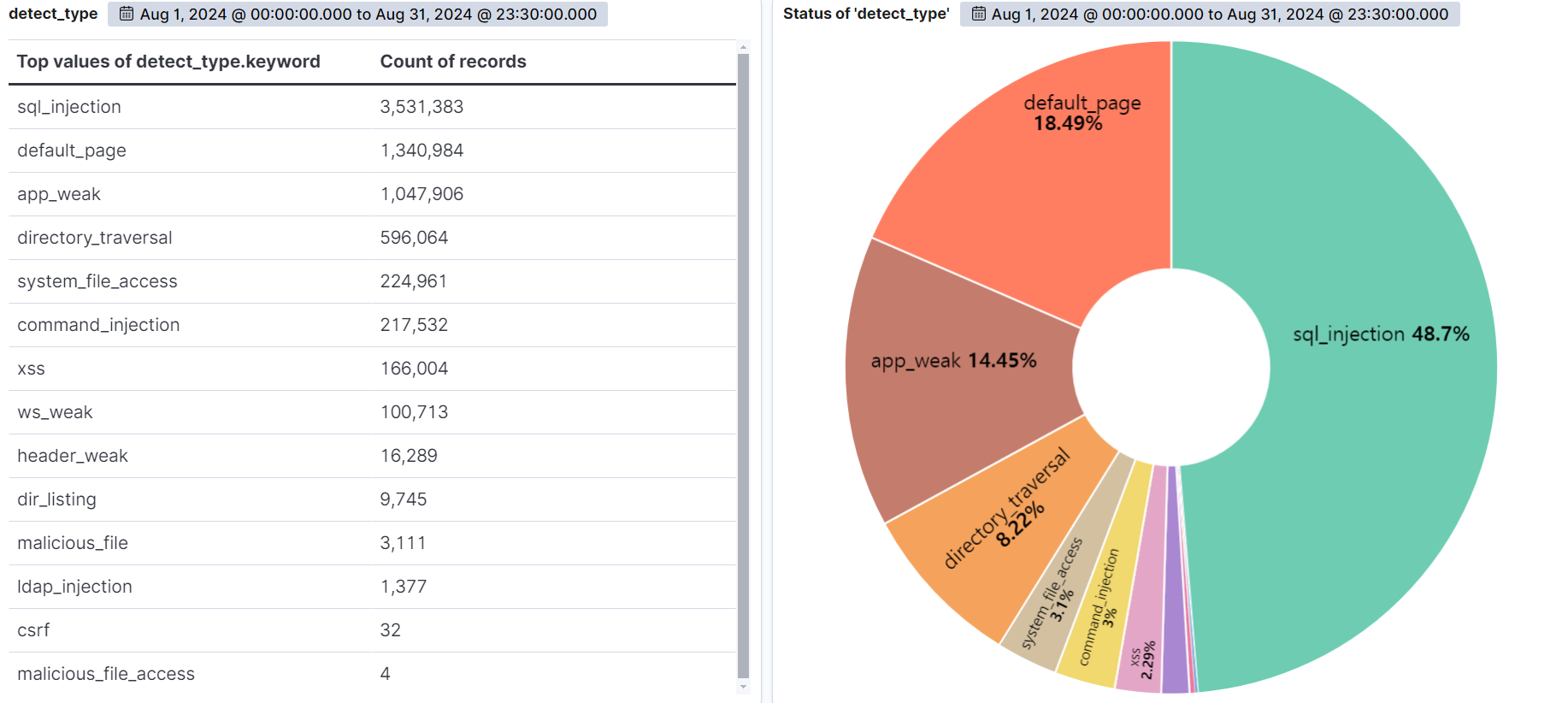
SQL Injection (48.7%) was the most common attack type, followed by Default Page (18.49%), Application Weakness (14.45%), and Directory Traversal (8.22%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP. It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results. If you encounter the following syntax in your query values, you should suspect an attack.
Default Page attempts to access a file from an unusual path or bypasses authorized files to access the file directly. These are not files typically used by the web service, so be suspicious of malicious intent.
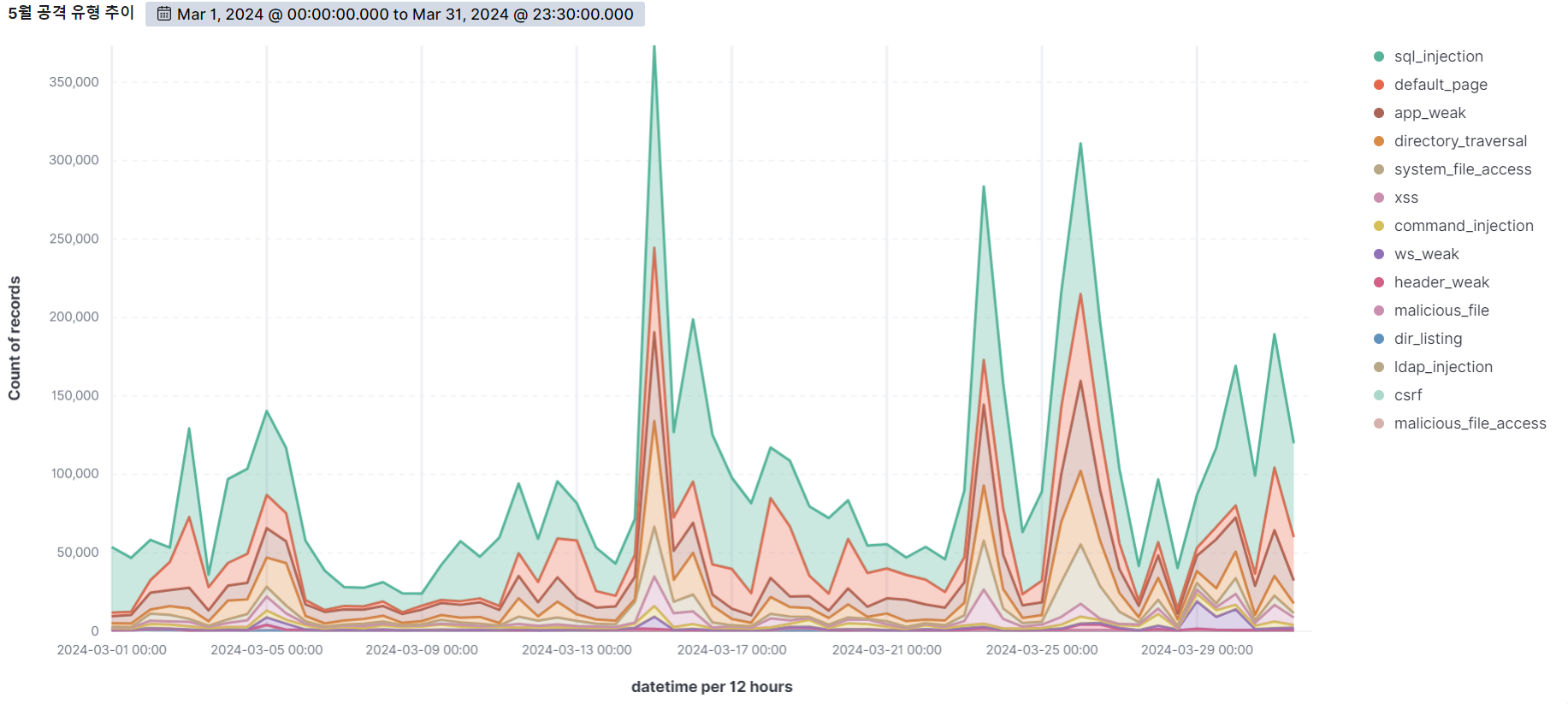
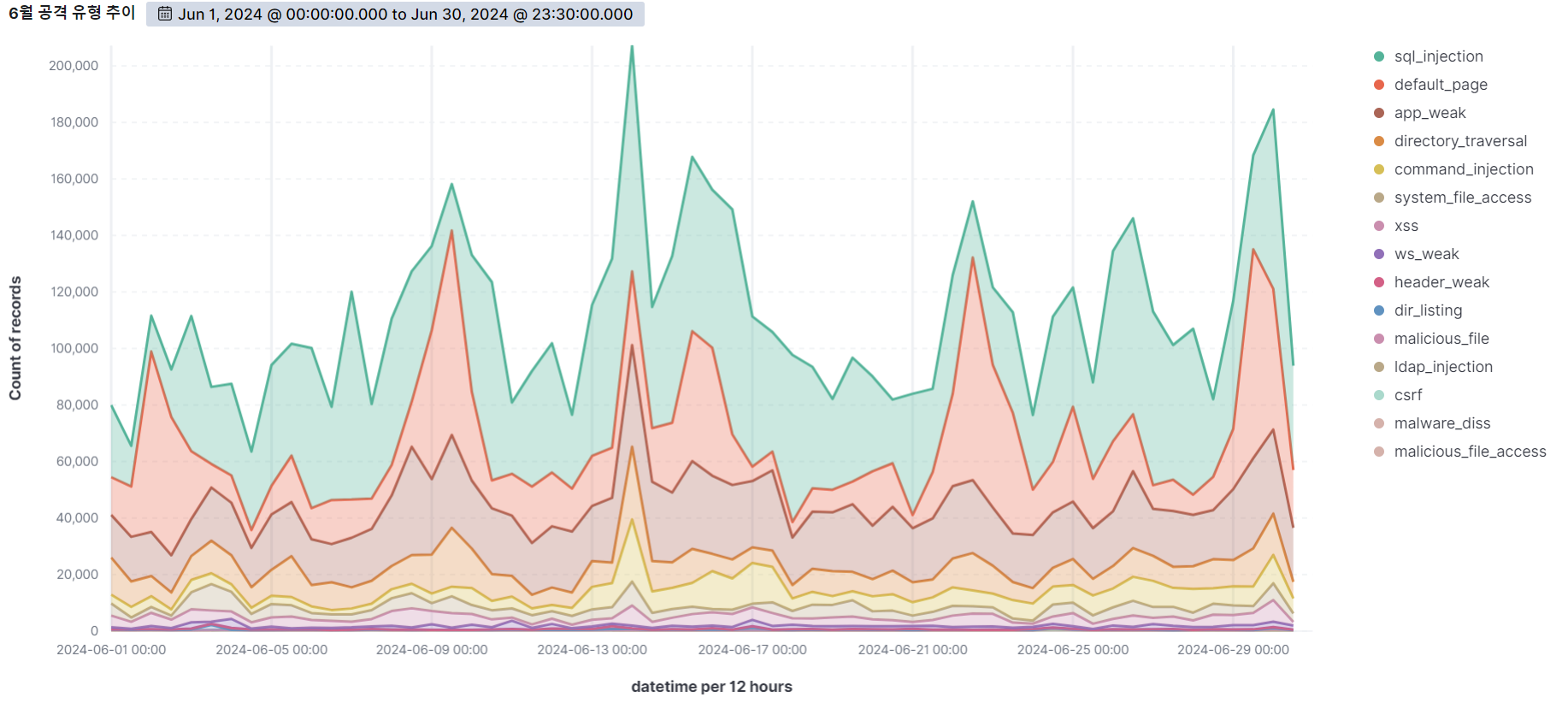
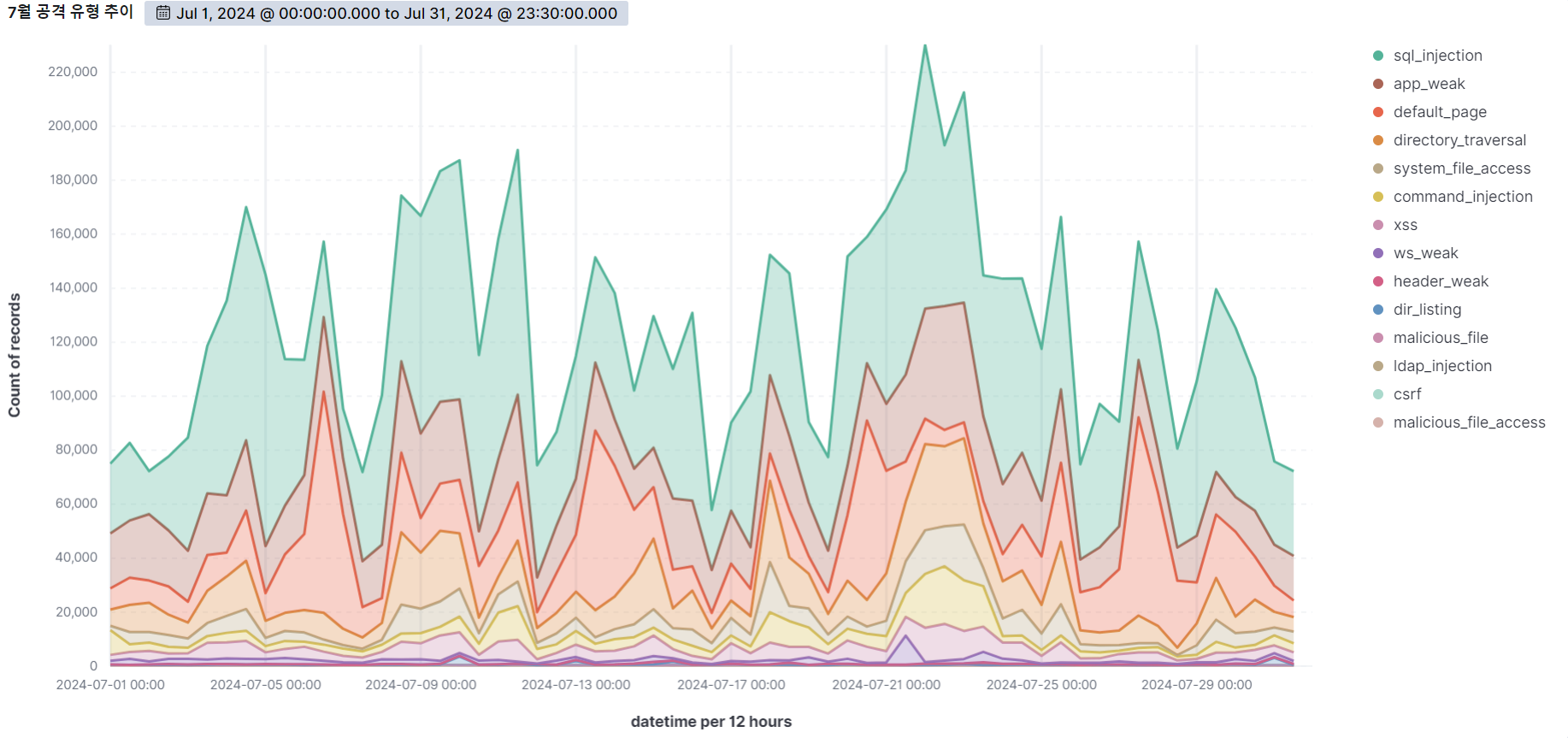
Summary of web attack trend graphs for the last 3 months
May
June
July
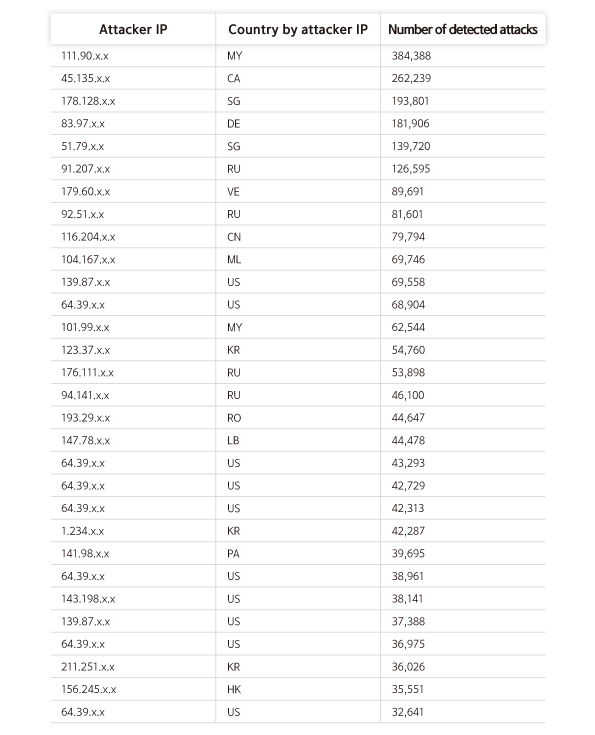
Top 30 Attacker IPs
Vulnerability analysis reports
[MS Office zero-day vulnerability Follina]
1. Overview
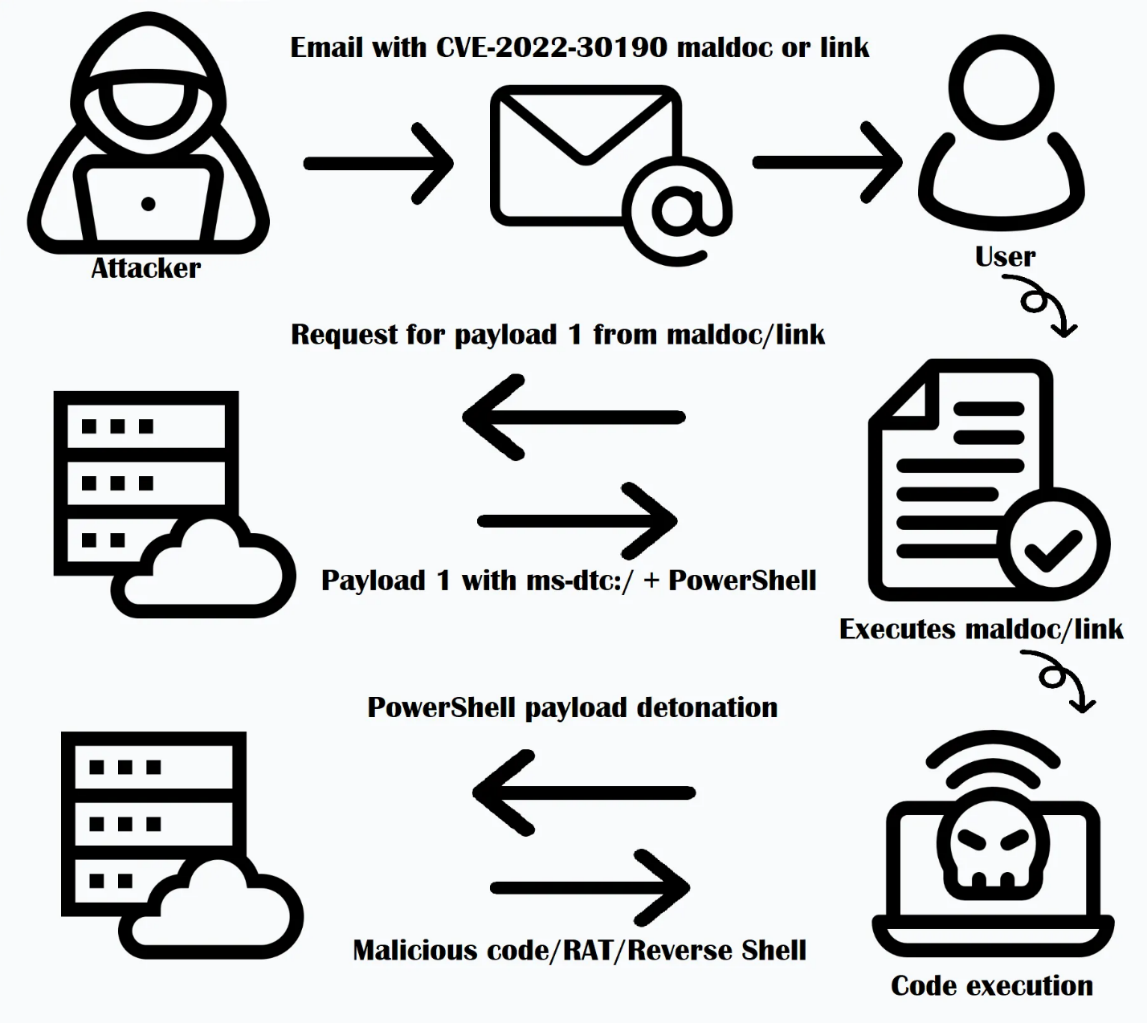
The vulnerability is a security flaw related to MS Office document handling functionality in Microsoft Windows. The vulnerability allows malicious code to be executed, specifically via Word documents, and could allow an attacker to execute remote code without victim intervention. CVE-2022-30190 occurs in the Microsoft Support Diagnostic Tool (MSDT) in Windows, and exploitation of this vulnerability could allow an attacker to perform remote code execution (RCE).

2. Attack types
In the Word document where the vulnerability was identified, the vulnerability occurred when the vulnerable HTML file was downloaded and executed via a URL link written in the External tag, a known method.
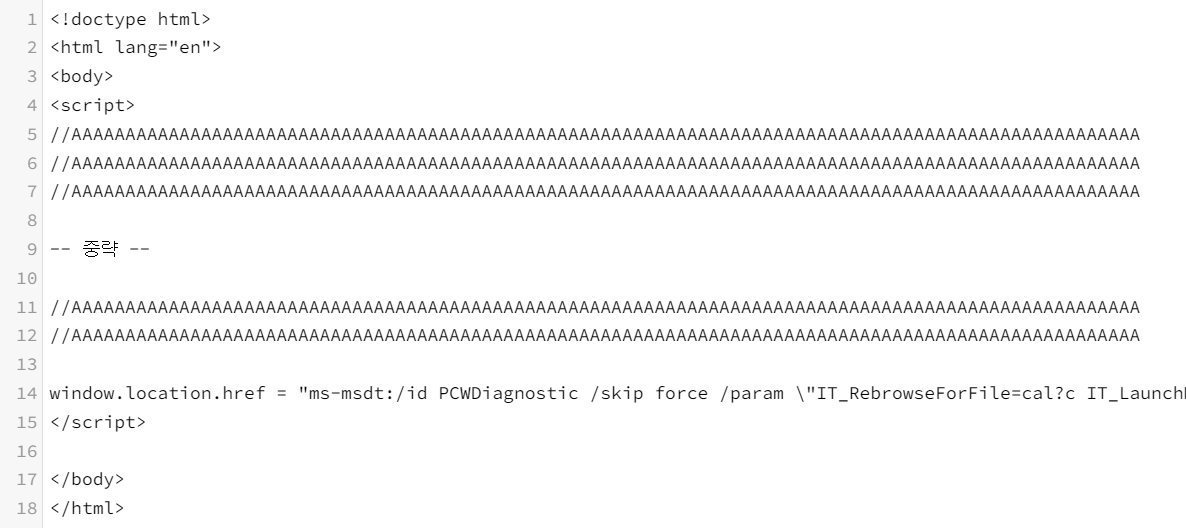
When a word document with the above code is forwarded to the victim by mail and further actions, and then opened or previewed, MSDT downloads and executes a malicious script on a remote server. This allows the attacker to execute arbitrary commands on the victim's computer.
3. What to do
The universal response to the Follina vulnerability is as follows
- Apply security patches: Immediately install security updates provided by Microsoft.
- Disable MSDT: Use a registry editor to disable the ms-msdt protocol.
- Beware of document files: Do not open documents from unknown sources, and be especially careful not to use the preview feature in Word documents.
Our AIWAF product detects protocols such as ms-msdt in the 316: Command Injection (ms-msdt) pattern, which is detected as normal.
4. Conclusion
CVE-2022-30190 is a vulnerability that poses a significant threat to MS Office users. If left untreated, it could allow an attacker to remotely execute malicious code and take over a victim's system. Therefore, it is imperative that you apply the latest security updates, disable the MSDT protocol, and take other security measures.
5. References
- https://www.vicarius.io/vsociety/posts/microsoft-support-diagnostic-tool-remote-code-execution-vulnerability-cve-2022-30190
- https://asec.ahnlab.com/ko/34919/
- https://blog.naver.com/best_somansa/222839504756
Latest vulnerability CVE status
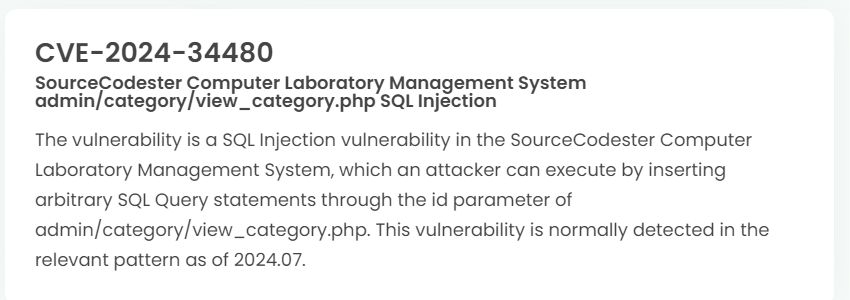
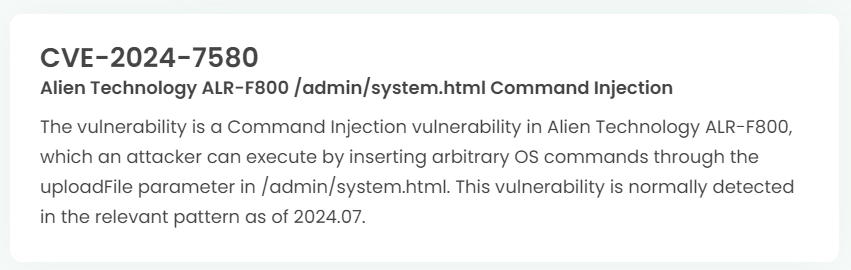
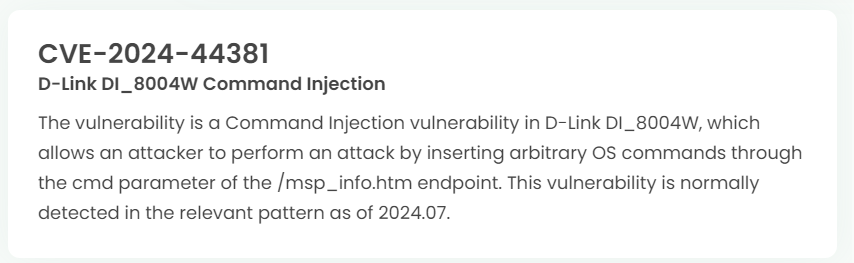
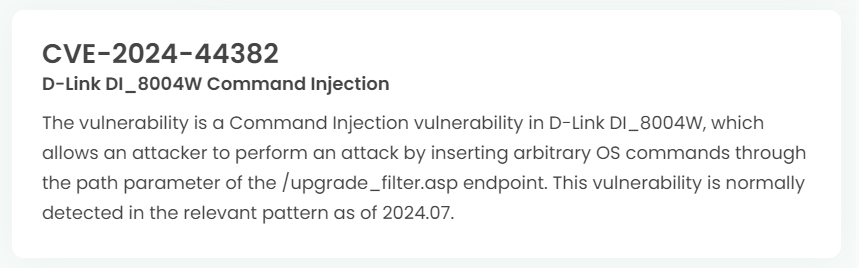
1. High-risk vulnerability status (2024.08)
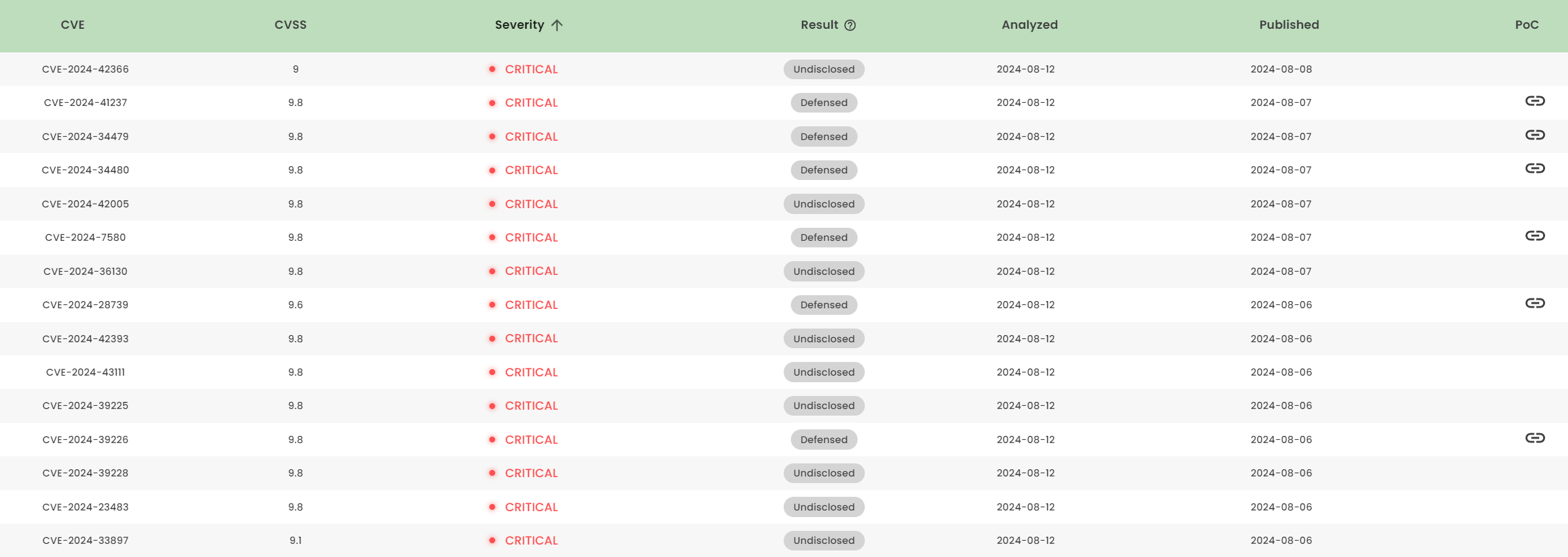
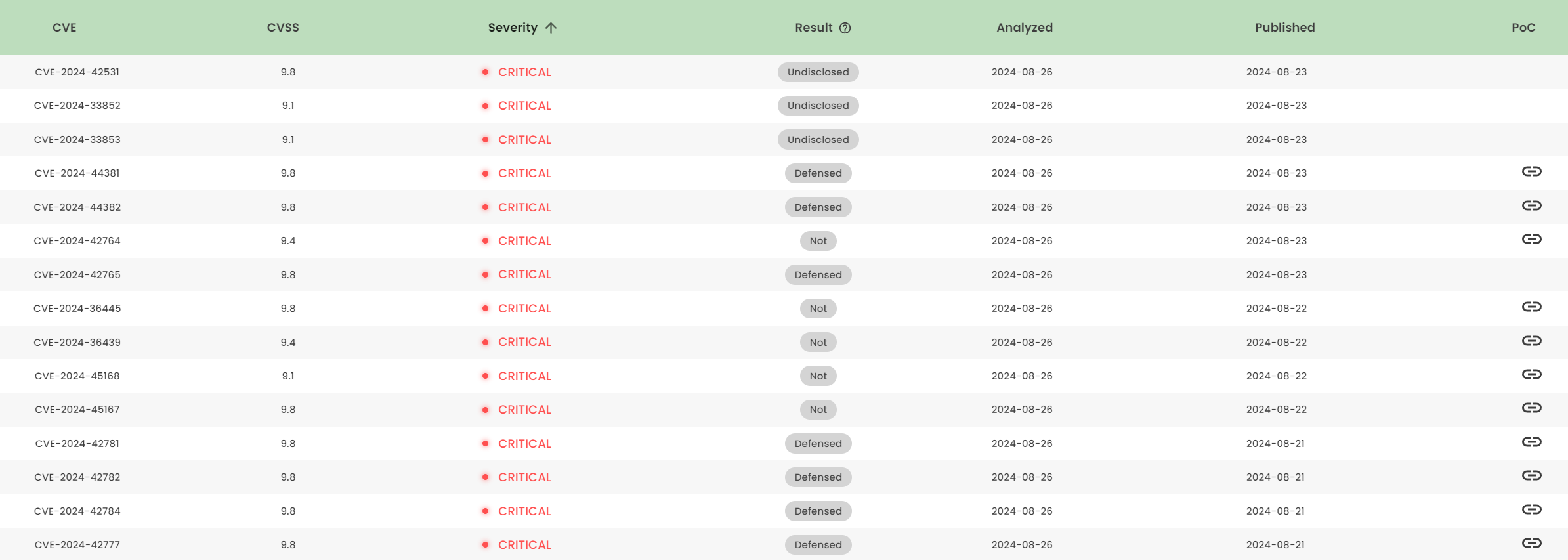
2. High-risk vulnerability descriptions